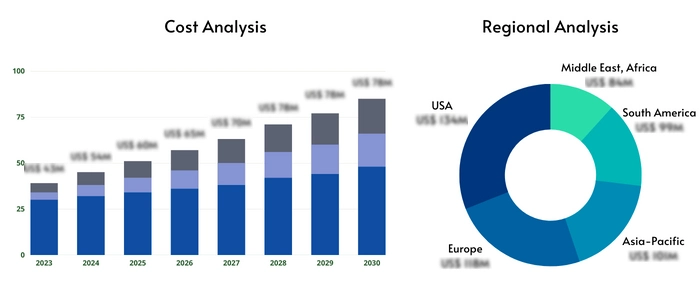
Bug Bounty Platforms Market Size Report By Type (Cloud, SaaS, Web, Mobile-Android Native, Mobile-iOS Native, Host), By Application (Finance & Banking, Software Development, Retail, Government, Other), By Region (North America, Latin America, Europe, Asia Pacific, Middle East, and Africa) - Share, Trends, Outlook and Forecast 2025-2033 (Financial Impact Analysis)
ID : MRU_ 404933 | Date : Mar, 2025 | Pages : 242 | Region : Global | Publisher : MRU
Introduction:
The Bug Bounty Platforms market is experiencing a period of significant growth, driven by the increasing awareness of cybersecurity threats and the need for proactive vulnerability management. Organizations across various sectors are increasingly relying on bug bounty programs to identify and remediate security flaws before malicious actors can exploit them. This proactive approach is far more cost-effective than reacting to breaches after they occur. The markets expansion is fueled by several key drivers. Firstly, the sophistication and frequency of cyberattacks are escalating, pushing organizations to adopt more robust security measures. Secondly, technological advancements, such as automation and AI-powered vulnerability scanning tools, are streamlining the bug bounty process, making it more efficient and accessible to a wider range of organizations. Thirdly, the rising adoption of cloud-based services and the increasing interconnectedness of digital systems have created a larger attack surface, further intensifying the demand for comprehensive security testing. This market plays a crucial role in addressing global challenges related to cybersecurity, helping to protect critical infrastructure, financial systems, and personal data from malicious attacks. The increasing reliance on digital technologies across all aspects of modern life makes robust cybersecurity paramount, and the bug bounty model is proving to be an effective and scalable solution. The collaborative nature of bug bounty programs, engaging security researchers globally, contributes to the rapid identification and resolution of vulnerabilities, significantly improving overall cybersecurity posture. Furthermore, the growing awareness of data privacy regulations, such as GDPR and CCPA, is driving organizations to strengthen their security practices and adopt measures like bug bounty programs to demonstrate compliance. The markets success hinges on the ability of platforms to provide a secure, efficient, and rewarding environment for researchers while simultaneously offering valuable insights to organizations looking to improve their security posture. The projected CAGR of XX% reflects this strong growth trajectory and underlines the markets importance in shaping the future of cybersecurity.
The Bug Bounty Platforms market is experiencing a period of significant growth, The projected CAGR of XX%
Market Scope and Overview:
The Bug Bounty Platforms market encompasses a range of software and services that facilitate the operation of bug bounty programs. These platforms connect organizations needing security assessments with security researchers (often referred to as \"ethical hackers\") who identify and report vulnerabilities. The technologies involved include vulnerability scanning tools, communication and collaboration features, reward management systems, and reporting dashboards. Applications span diverse industries, including finance & banking, software development, retail, government, and more. The markets importance lies in its ability to leverage the collective expertise of a global community of security researchers to identify vulnerabilities that might otherwise remain undetected. This proactive approach is a departure from traditional, reactive security models. In the context of global trends, the markets growth is strongly linked to several factors: the increasing reliance on digital technologies, the growth of the cloud computing market, the heightened awareness of cybersecurity threats, and the increasing stringency of data privacy regulations. The market is also influenced by evolving cyberattack techniques and the growing sophistication of malicious actors. By providing a structured and incentivized framework for vulnerability discovery, bug bounty platforms contribute significantly to improving the overall cybersecurity landscape. Their role in mitigating risk and reducing the financial and reputational impact of cyber breaches is becoming increasingly crucial as organizations face an ever-evolving threat landscape. The markets continued growth will depend on its capacity to adapt to emerging threats, integrate new technologies, and effectively manage the complex legal and ethical considerations involved in vulnerability reporting.
Definition of Market:
The Bug Bounty Platforms market refers to the ecosystem of software and services designed to support and manage bug bounty programs. These programs incentivize security researchers to identify vulnerabilities in an organizations systems or applications in exchange for monetary rewards or other forms of compensation. The market encompasses several key components: The platforms themselves, which offer features such as vulnerability submission, triage, validation, and reward payment; the security researchers who actively participate in bug bounty programs; the organizations that sponsor bug bounty programs to improve their security posture; and the supporting infrastructure, such as payment processors and legal frameworks. Key terms associated with the market include: \"bug bounty,\" \"vulnerability disclosure program (VDP),\" \"ethical hacking,\" \"pentesting,\" \"responsible disclosure,\" \"vulnerability management,\" \"zero-day exploit,\" and \"security researcher.\" Understanding these terms is vital for comprehending the markets dynamics. A \"bug bounty\" is essentially a reward offered for the discovery and responsible disclosure of a security vulnerability. \"Ethical hacking\" refers to the practice of using hacking techniques to identify vulnerabilities for the purpose of improving security. \"Responsible disclosure\" emphasizes the importance of reporting vulnerabilities ethically and in a way that minimizes potential harm. \"Vulnerability management\" covers the entire process of identifying, assessing, and mitigating security risks. The market operates on the principle of incentivized vulnerability disclosure, turning potential security threats into opportunities for improvement and collaboration between organizations and the security research community. The effective management and integration of these various components are essential for the success and growth of the bug bounty platform market.
Market Segmentation:
The Bug Bounty Platforms market can be segmented based on type, application, and end-user. This segmentation helps in understanding the specific needs and characteristics of different market segments and their contributions to overall market growth. Each segment exhibits unique dynamics and growth potentials, shaped by technological advancements, industry-specific security requirements, and regulatory landscapes. Analyzing these segments allows for a more granular understanding of the markets overall health and future trajectory.
By Type:
Cloud: Cloud-based bug bounty platforms offer scalability, accessibility, and ease of use. They allow organizations of all sizes to easily launch and manage bug bounty programs without significant upfront infrastructure investment. Their flexibility and cost-effectiveness are key drivers of adoption. They are particularly appealing to organizations lacking in-house cybersecurity expertise.
SaaS: Software-as-a-Service (SaaS) platforms provide a subscription-based model for accessing bug bounty features, enabling organizations to scale their programs as needed. This approach facilitates pay-as-you-go pricing, making it a cost-effective option for organizations with varying security needs. The simplicity and ease of integration are significant advantages.
Web: Web-based platforms offer browser access and compatibility across different operating systems. Their accessibility and user-friendliness contribute to their widespread adoption. Ease of access is a crucial element for both researchers and organizations.
Mobile-Android Native: Native Android applications provide a seamless and optimized user experience specifically tailored for Android devices. This segment benefits from the growing adoption of mobile devices for security research and reporting.
Mobile-iOS Native: Similar to Android-native platforms, iOS-native applications cater specifically to iOS users, providing optimized functionality and performance on Apple devices. The segment growth mirrors the increasing use of iOS devices in professional and personal settings.
Host: These platforms may offer on-premise solutions or hybrid deployments, offering greater control and customization for organizations with specific security requirements and infrastructure constraints. They are beneficial for organizations needing enhanced security or particular integration capabilities.
By Application:
The diverse applications of bug bounty platforms reflect the widespread need for enhanced cybersecurity across various sectors. Finance & banking, with their critical reliance on secure systems, are prominent adopters. Software development organizations use them to test their products pre-release. Retail businesses utilize these platforms to protect sensitive customer data. Government agencies depend on them to safeguard critical infrastructure and sensitive information. Other industries, from healthcare to energy, are increasingly turning to these platforms to fortify their security postures.
By End User:
Governments are increasingly adopting bug bounty programs to bolster national cybersecurity. Businesses across various sectors are actively using these platforms to identify and remediate vulnerabilities. Individuals, while not directly using platforms, benefit from the improved security of the systems they interact with. The collaborative nature of the ecosystem involves all three stakeholders significantly.
Market Outlook and Projections:
| Report Attributes | Report Details |
| Base year | 2024 |
| Forecast year | 2025-2033 |
| CAGR % | XX |
| Segments Covered | Key Players, Types, Applications, End-Users, and more |
| Major Players | Bugcrowd, Synack, HackerOne, Yes We Hack, HackenProof, Cobalt, intigriti, SafeHats, HACKTROPHY, Zerocopter, PlugBounty |
| Types | Cloud, SaaS, Web, Mobile-Android Native, Mobile-iOS Native, Host |
| Applications | Finance & Banking, Software Development, Retail, Government, Other |
| Industry Coverage | Total Revenue Forecast, Company Ranking and Market Share, Regional Competitive Landscape, Growth Factors, New Trends, Business Strategies, and more |
| Region Analysis | North America, Europe, Asia Pacific, Latin America, Middle East and Africa |
The Top Key Market Players for Bug Bounty Platforms Market Listed are:
Bugcrowd
Synack
HackerOne
Yes We Hack
HackenProof
Cobalt
intigriti
SafeHats
HACKTROPHY
Zerocopter
PlugBounty
Market Drivers:
Several factors are driving the growth of the Bug Bounty Platforms market: The increasing frequency and sophistication of cyberattacks, forcing organizations to adopt more robust security measures; the rising adoption of cloud-based services and the expansion of the attack surface; the growing awareness of data privacy regulations and the need for compliance; the availability of advanced vulnerability scanning tools and AI-powered solutions; government initiatives promoting cybersecurity awareness and best practices; and the increasing availability of skilled security researchers.
Market Restraints:
Challenges facing the market include: The high initial cost of implementing a bug bounty program for some organizations; the need for skilled personnel to manage and coordinate the program; the potential for false positives and the need for efficient vulnerability validation processes; the legal and ethical considerations around vulnerability disclosure; and concerns about the potential for misuse of the platform by malicious actors.
Market Opportunities:
Growth prospects exist in expanding into new geographic regions, integrating new technologies such as AI and machine learning for improved vulnerability detection, developing specialized platforms for specific industries, and offering enhanced reporting and analytics capabilities. Innovations in automated vulnerability assessment, streamlined communication tools, and advanced reward systems will drive further market expansion.
Market Challenges:
The Bug Bounty Platforms market faces several significant challenges. Firstly, the complexity of managing bug bounty programs can be overwhelming for organizations lacking dedicated cybersecurity expertise. Effective program management requires a deep understanding of vulnerability assessment, ethical hacking practices, and legal frameworks surrounding responsible disclosure. Secondly, ensuring the quality and reliability of vulnerability reports is crucial. False positives and poorly documented vulnerabilities can waste valuable time and resources. Thirdly, establishing clear and consistent reward structures is vital to incentivize participation from skilled security researchers. Fair and competitive rewards are essential for attracting the best talent. Fourthly, navigating legal and ethical considerations related to vulnerability disclosure is paramount. Organizations must comply with relevant regulations and ensure responsible disclosure practices to avoid potential legal issues. Fifthly, scaling bug bounty programs to handle increasing volumes of vulnerability reports can be challenging. Efficient triage and validation processes are necessary to manage the workflow effectively. Finally, securing the platform itself from malicious actors is a critical challenge. Bug bounty platforms must be highly secure to prevent compromise and ensure the integrity of the vulnerability reporting process. Addressing these challenges will require continuous innovation and improvement in platform technology, program management best practices, and collaborative efforts between organizations and security researchers.
Market Key Trends:
Key trends include: Increased adoption of automated vulnerability scanning tools; the integration of AI and machine learning for improved vulnerability detection and analysis; the emergence of specialized platforms catering to specific industries; a shift towards more transparent and collaborative vulnerability disclosure practices; the growing emphasis on responsible disclosure and ethical hacking principles; and the increasing adoption of bug bounty programs by governments and critical infrastructure organizations.
Market Regional Analysis:
North America currently holds a significant share of the market, driven by high cybersecurity awareness, a large number of skilled security researchers, and a robust technology ecosystem. Europe is also a significant market, with growing regulatory pressure driving the adoption of bug bounty programs. Asia Pacific is experiencing rapid growth, fueled by increasing digitalization and a growing awareness of cybersecurity threats. Latin America and the Middle East & Africa are emerging markets with significant growth potential, as cybersecurity awareness and digital infrastructure continue to develop. Each region presents unique opportunities and challenges, shaped by factors such as regulatory landscapes, technological maturity, and the availability of skilled security professionals. North Americas established market position benefits from a high concentration of technology companies and a strong security culture. Europes growth is influenced by stringent data privacy regulations, while Asia Pacifics rapid expansion is driven by its burgeoning digital economy. Emerging markets present opportunities for platform providers to reach new customer segments, but success in these regions depends on tailoring services to local contexts and addressing specific market needs.
Regional Analysis For Bug Bounty Platforms Market
- United States, Canada, and Mexico Germany, France, UK, Russia, and Italy China, Japan, Korea, India, and Southeast Asia Brazil, Argentina, Colombia Middle East and Africa
Frequently Asked Questions:
Q: What is the projected growth of the Bug Bounty Platforms market from 2025 to 2033?
A: The Bug Bounty Platforms market is projected to grow at a CAGR of XX% from 2025 to 2033.
Q: What are the key trends shaping the Bug Bounty Platforms market?
A: Key trends include the increasing adoption of automated vulnerability scanning, the integration of AI and machine learning, and the emergence of specialized platforms for various industries.
Q: What are the most popular types of Bug Bounty Platforms?
A: Cloud-based and SaaS platforms are currently the most popular types, due to their scalability, accessibility, and ease of use.
Q: What are the main challenges facing the Bug Bounty Platforms market?
A: Challenges include the need for skilled personnel to manage programs, ensuring the quality of vulnerability reports, establishing clear reward structures, and navigating legal and ethical considerations.
Q: What are the future growth opportunities for the Bug Bounty Platforms market?
A: Future opportunities include expanding into new geographic regions, developing specialized platforms for specific industries, and integrating advanced technologies to improve vulnerability detection and analysis.
Research Methodology
The Market Research Update offers technology-driven solutions and its full integration in the research process to be skilled at every step. We use diverse assets to produce the best results for our clients. The success of a research project is completely reliant on the research process adopted by the company. Market Research Update assists its clients to recognize opportunities by examining the global market and offering economic insights. We are proud of our extensive coverage that encompasses the understanding of numerous major industry domains.
Market Research Update provide consistency in our research report, also we provide on the part of the analysis of forecast across a gamut of coverage geographies and coverage. The research teams carry out primary and secondary research to implement and design the data collection procedure. The research team then analyzes data about the latest trends and major issues in reference to each industry and country. This helps to determine the anticipated market-related procedures in the future. The company offers technology-driven solutions and its full incorporation in the research method to be skilled at each step.
The Company's Research Process Has the Following Advantages:
- Information Procurement
The step comprises the procurement of market-related information or data via different methodologies & sources.
- Information Investigation
This step comprises the mapping and investigation of all the information procured from the earlier step. It also includes the analysis of data differences observed across numerous data sources.
- Highly Authentic Source
We offer highly authentic information from numerous sources. To fulfills the client’s requirement.
- Market Formulation
This step entails the placement of data points at suitable market spaces in an effort to assume possible conclusions. Analyst viewpoint and subject matter specialist based examining the form of market sizing also plays an essential role in this step.
- Validation & Publishing of Information
Validation is a significant step in the procedure. Validation via an intricately designed procedure assists us to conclude data-points to be used for final calculations.
Request Free Sample:
Related Reports
- Bug Bounty Platforms Market Statistics 2023 Analysis By Application (Finance & Banking, Software Development, Retail, Government, Other), By Type (Cloud, SaaS, Web, Mobile - Android Native, Host), and By Region (North America, Latin America, Europe, Asia Pacific, Middle East, and Africa) - Size, Share, Outlook, and Forecast 2023 to 2030
- Bug Bounty Platforms Market Size, Share, Trends, & Covid-19 Impact Analysis By Type (Cloud, SaaS, Web, Mobile - Android Native, Host), By Application (Finance & Banking, Software Development, Retail, Government, Other), By Region - North America, Latin America, Europe, Asia Pacific, Middle East, and Africa | In-depth Analysis of all factors and Forecast 2023-2030
- Bug Bounty Platforms Market Size By Regional(Europe, North America, South America, Asia Pacific, Middle East And Africa), Industry Growth Opportunity, Price Trends, Competitive Shares, Market Statistics and Forecasts 2023 - 2030
- Bug Bounty Platforms Market Size By Demand, By Type, By Application, Regional Analysis(Europe, Asia Pacific, America, Middle East And Africa), And Forecasts 2023 - 2030
- Bug Bounty Platforms Market Size, Analysis By Application, Regional Analysis(Europe[Germany, UK, France, Italy, Russia, Spain, Netherlands, Turkey, Switzerland], Asia Pacific[China, Southeast Asia, India, Japan, Korea, Western Asia], America[United States, Canada, Mexico, Brazil, Argentina, Columbia, Chile, Peru], Middle East And Africa), And Forecasts 2023-2030


We're cost-effective and Offered Best services:
We are flexible and responsive startup research firm. We adapt as your research requires change, with cost-effectiveness and highly researched report that larger companies can't match.

Information Safety
Market Research Update ensure that we deliver best reports. We care about the confidential and personal information quality, safety, of reports. We use Authorize secure payment process.

We Are Committed to Quality and Deadlines
We offer quality of reports within deadlines. We've worked hard to find the best ways to offer our customers results-oriented and process driven consulting services.

Our Remarkable Track Record
We concentrate on developing lasting and strong client relationship. At present, we hold numerous preferred relationships with industry leading firms that have relied on us constantly for their research requirements.

Best Service Assured
Buy reports from our executives that best suits your need and helps you stay ahead of the competition.

Customized Research Reports
Our research services are custom-made especially to you and your firm in order to discover practical growth recommendations and strategies. We don't stick to a one size fits all strategy. We appreciate that your business has particular research necessities.

Service Assurance
At Market Research Update, we are dedicated to offer the best probable recommendations and service to all our clients. You will be able to speak to experienced analyst who will be aware of your research requirements precisely.
The content of the report is always up to the mark. Good to see speakers from expertise authorities.
Privacy requested , Managing Director
A lot of unique and interesting topics which are described in good manner.
Privacy requested, President
Well researched, expertise analysts, well organized, concrete and current topics delivered in time.
Privacy requested, Development Manager