Cyber Range Market Size By Region (North America, Europe, Asia-Pacific, Latin America, Middle East and Africa), By Statistics, Trends, Outlook and Forecast 2026 to 2033 (Financial Impact Analysis)
ID : MRU_ 437669 | Date : Dec, 2025 | Pages : 253 | Region : Global | Publisher : MRU
Cyber Range Market Size
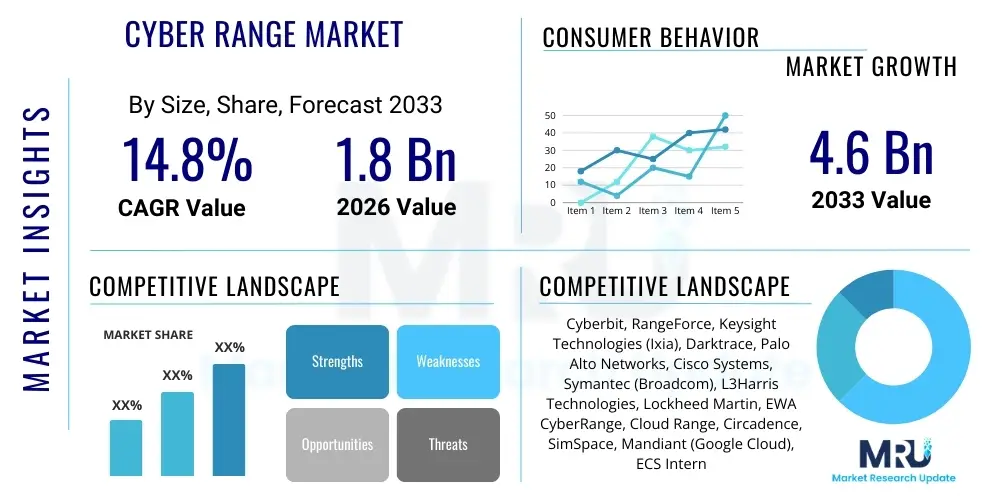
The Cyber Range Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 14.8% between 2026 and 2033. The market is estimated at $1.8 Billion USD in 2026 and is projected to reach $4.6 Billion USD by the end of the forecast period in 2033. This substantial expansion is fundamentally driven by the escalating frequency and sophistication of cyber threats globally, compelling organizations across all sectors—particularly government, defense, and BFSI—to invest heavily in advanced, realistic simulation environments for comprehensive cybersecurity training and readiness assessment.
The valuation reflects the critical necessity for organizations to establish proactive defense mechanisms capable of handling zero-day exploits and complex, multi-stage attacks. Market growth is further accelerated by increasing government mandates requiring robust cybersecurity readiness testing, coupled with the persistent shortage of skilled cybersecurity professionals worldwide. Cyber ranges offer the ideal platform to bridge this skills gap by providing hands-on, high-fidelity environments where teams can practice incident response protocols under pressure without jeopardizing live operational infrastructure, thereby enhancing organizational cyber resilience and minimizing potential financial and reputational losses associated with breaches.
Cyber Range Market introduction
The Cyber Range Market encompasses sophisticated, virtualized platforms designed to simulate realistic network environments, systems, applications, and attack scenarios, providing a safe, controlled space for individuals and teams to practice cybersecurity defense, attack, and incident response skills. These platforms emulate complex organizational networks, allowing users to engage in hands-on training, competency development, and validation of security tools and procedures against live cyber threats or simulated attacks, ensuring readiness across the entire threat spectrum. Products range from cloud-based subscription models offering accessibility and scalability to fully customized, on-premise hardware solutions tailored for highly sensitive government or defense applications. Key objectives include workforce skill enhancement, validation of defensive architectures, and fostering collaborative security team development through scenario-based learning.
Major applications of cyber ranges span across professional training, certification, workforce development, security product testing (sandboxing), and national cyber defense exercises. In corporate settings, they are indispensable for continuous security education and testing new hires' defensive capabilities. The primary benefits derived from the adoption of cyber range solutions include enhanced organizational cyber resilience, measurable improvement in incident response times, cost-effective training delivery compared to live infrastructure testing, and the ability to accurately assess the effectiveness of existing security controls and technologies. Furthermore, they play a crucial role in validating compliance with evolving regulatory standards that demand verifiable proof of security preparedness and staff competency, particularly within highly regulated industries such as finance and healthcare.
The market is predominantly driven by three critical factors: the widening global cybersecurity skills gap, the increasing frequency and complexity of state-sponsored and criminal cyber attacks requiring continuous upskilling, and the rapid migration of enterprise infrastructure to multi-cloud and hybrid environments which necessitates complex, high-fidelity simulation for accurate risk assessment. Additionally, the proliferation of specialized threat intelligence and the need for realistic red team/blue team exercises are boosting demand for advanced cyber range capabilities that can mirror current geopolitical and technical threat landscapes with precision and scale. These combined forces ensure sustained, high-growth investment in realistic simulation platforms across governmental and commercial sectors seeking to maintain a defensive advantage.
Cyber Range Market Executive Summary
The Cyber Range Market is undergoing robust expansion, characterized by significant shifts towards highly scalable, cloud-delivered platforms leveraging advanced automation and AI-driven scenario generation. Business trends indicate a strong move away from traditional, physical lab environments to virtualized, subscription-based models (Cyber Range as a Service, CRaaS), which drastically lowers entry barriers and allows for flexible, on-demand capacity scaling tailored to specific training needs, driving high adoption among Small and Medium-sized Enterprises (SMEs) that previously lacked the capital for dedicated physical infrastructure. Furthermore, vendor competition is intensifying, focusing on specialized content libraries and integration capabilities with existing enterprise security stacks (SIEM, SOAR) to provide integrated defense workflow training, enhancing the platform's utility beyond mere theoretical exercises into practical, operational preparedness simulations.
Regionally, North America maintains the dominant market share, primarily due to high defense spending, the early adoption of advanced security technologies, and the strict regulatory frameworks requiring demonstrably competent security teams, particularly in the United States federal sector and critical infrastructure domain. However, the Asia Pacific (APAC) region is projected to exhibit the highest Compound Annual Growth Rate (CAGR) over the forecast period, fueled by rapid digital transformation initiatives, increasing awareness of cyber threats in developing economies like India and China, and substantial government investments aimed at building national cyber workforce resilience. Europe is also witnessing healthy growth, spurred by GDPR compliance pressures and strategic initiatives to standardize cybersecurity capabilities across the European Union member states.
Segment trends reveal that the Services component, encompassing professional services like customized scenario development, platform maintenance, and expert mentorship, holds a substantial share, reflecting the complexity involved in maintaining and utilizing these advanced platforms effectively, often requiring external specialized support. Technology-wise, the adoption of advanced networking virtualization technologies and specialized containerization for creating isolated, reproducible environments is accelerating. The end-user segmentation continues to be dominated by BFSI, IT & Telecom, and Defense sectors, though there is emerging high growth in the healthcare and utilities sectors recognizing their vulnerability to operational technology (OT) attacks and ransomware campaigns, consequently driving demand for tailored OT/IT convergence simulation scenarios.
AI Impact Analysis on Cyber Range Market
User questions frequently center on how Artificial Intelligence (AI) and Machine Learning (ML) are transforming both the threat landscape and the utility of cyber ranges, specifically querying whether AI can automate scenario generation, grade trainee performance objectively, or simulate sophisticated, adaptive attackers (Adversarial AI). Users are concerned about the ability of static training modules to prepare professionals against AI-enhanced malware and autonomous exploits. Analysis reveals that the key expectation is for AI to elevate cyber range capabilities from predefined scripts to dynamic, complex, and evolving threat simulations, thereby providing training environments that more accurately reflect real-world, modern attacks which often utilize ML to optimize evasion techniques and target selection. This necessitates AI implementation for high-fidelity attacker emulation and predictive analytics within the range infrastructure itself.
The immediate impact of AI is seen in the automation of lab environment provisioning and the dynamic orchestration of training scenarios. AI algorithms are being deployed to analyze a trainee's performance in real-time, adjusting the difficulty and complexity of the simulated attack path based on the user's observed actions and skill level, ensuring personalized and optimally challenging learning experiences. This dramatically increases the efficacy of training sessions and reduces the instructor workload associated with manual scenario adjustments and post-exercise debriefings. Furthermore, AI contributes significantly to the creation of massive, diverse datasets required to train and test next-generation security tools, utilizing the cyber range as a controlled data factory for security product validation.
In the long term, the integration of Generative AI capabilities promises to revolutionize content creation within cyber ranges, enabling the rapid development of novel, highly contextualized threat scenarios that mirror emerging geopolitical conflicts or industry-specific vulnerabilities without extensive manual programming. This capability ensures that training remains perpetually relevant to the evolving threat matrix. However, a major concern remains the "AI gap"—ensuring that the defense mechanisms trained in the range are prepared to combat attacks launched by increasingly advanced Adversarial AI systems, pushing cyber range operators to continuously update their simulation tools with cutting-edge defensive countermeasures and detection models.
- AI-powered dynamic scenario generation increases realism and training relevance.
- Machine Learning is utilized for automated performance grading and skill assessment validation.
- Adversarial AI simulates sophisticated, adaptive attacker behaviors, challenging defensive teams.
- AI enhances the automation of environment provisioning and resource scaling within the range platform.
- Predictive analytics identifies trainee skill gaps and recommends personalized learning paths.
- Cyber ranges serve as crucial sandboxes for training and testing AI-driven security tools (e.g., automated threat detection systems).
DRO & Impact Forces Of Cyber Range Market
The Cyber Range Market is shaped by powerful driving forces centered around the global need for immediate cybersecurity readiness and workforce competence, yet restrained by high initial investment costs and complexity of deployment. Key drivers include escalating global cybercrime rates, mandates from regulatory bodies requiring demonstrated security preparedness (like DORA in finance or NIS 2 in Europe), and the recognized critical shortage of skilled cyber defenders. These factors collectively push organizations towards high-fidelity simulation environments as the most effective means to rapidly upskill and assess their teams. Opportunities are vast, particularly in leveraging cloud delivery models (CRaaS) for broader market penetration into SMEs and expanding offerings to include specialized simulations for Operational Technology (OT), Industrial Control Systems (ICS), and Internet of Things (IoT) security, areas where traditional training methodologies fall short and physical testing is highly risky. The primary restraints revolve around the significant capital expenditure required for sophisticated physical ranges, coupled with the ongoing difficulty in recruiting and retaining skilled trainers and content developers necessary to maintain relevance and efficacy of the training scenarios provided within the platform, alongside concerns regarding data isolation and security in multi-tenant cloud ranges.
The impact forces influencing market direction are multifaceted. Rapid technological change dictates the need for constant updates; a cyber range is only valuable if it accurately reflects the latest vulnerabilities and attack techniques, placing enormous pressure on vendors for continuous content refresh cycles. Furthermore, geopolitical tensions are directly impacting demand, particularly in government and critical infrastructure sectors, where the need to simulate nation-state-level attacks is paramount, driving significant investment in highly protected, isolated range environments capable of simulating catastrophic failure scenarios. The shift toward hybrid work models also acts as an impact force, necessitating training scenarios that account for distributed endpoint security risks and complex VPN or zero-trust architecture failures, requiring vendors to virtualize diverse user environment configurations.
The overall impact of these forces is overwhelmingly positive for market growth, skewing heavily towards the acceleration of CRaaS adoption and specialization of service offerings. While initial deployment hurdles exist, the catastrophic potential financial and reputational losses resulting from a major breach far outweigh the cost of implementing a robust cyber range solution. Consequently, organizations are prioritizing readiness and viewing cyber range expenditures not merely as a training expense but as a vital risk mitigation strategy, ensuring the market trajectory remains upward and competitive intensity focuses on content quality and platform scalability rather than price competition.
Segmentation Analysis
The Cyber Range Market is systematically segmented based on Component, Deployment, Technology, Application, End-User, and Region, reflecting the diverse needs of organizations requiring simulated defense environments. The Component segmentation, comprising Platforms (Software/Hardware) and Services (Professional and Managed), reveals a shift toward service-intensive offerings, as the complexity of maintaining cutting-edge scenarios and ensuring platform efficacy necessitates specialized support. Deployment models dictate accessibility, with Cloud-based solutions gaining rapid momentum due to lower TCO and enhanced scalability, contrasting with On-premise solutions favored by highly security-conscious government and defense organizations requiring absolute data control and isolation. This intricate segmentation allows vendors to target specific market niches, tailoring complexity, fidelity, and delivery mechanisms to optimize customer value proposition based on security maturity and budget constraints.
Further granularity is achieved through Application segmentation, highlighting distinct use cases such as Security Incident Response Training, Cyber Competition & Assessment, Vulnerability Research, and Product Testing. This shows that cyber ranges are utilized beyond simple training, extending into strategic organizational testing and validation functions, often blurring the lines between training and operational technology testing. The End-User analysis confirms BFSI, IT & Telecom, and Defense as major revenue contributors, but the increasing realization of systemic risk in Critical Infrastructure sectors (Energy, Healthcare, Utilities) is opening up substantial new market potential for specialized OT/ICS training modules that focus on physical consequences of cyber intrusion, driving segment growth diversification.
The dominance of services and cloud deployment models is fundamentally shaping market dynamics. The technical expertise required to develop and execute realistic, nation-state level attack scenarios is often beyond the capability of in-house security teams, pushing demand towards outsourced managed services. This reliance on expert-driven content and scenario development ensures continuous market relevance, contrasting with generic, static training content, making the Services segment a high-value and high-growth area within the broader cyber range ecosystem, critical for sustaining high-fidelity training capabilities required for effective modern defense.
- Component:
- Platforms (Software/Hardware/Virtualization Tools)
- Services (Professional Services, Managed Services, Support and Maintenance)
- Deployment Model:
- Cloud-based (CRaaS)
- On-premise
- Hybrid
- Technology:
- Virtualization (VMware, Hyper-V)
- Containerization (Docker, Kubernetes)
- Network Simulation Tools
- Application:
- Cybersecurity Training and Certification
- Security Incident Response (IR) Drills
- Red Teaming/Blue Teaming Exercises
- Product and Tool Validation (Sandbox Testing)
- Vulnerability Research
- End-User:
- BFSI (Banking, Financial Services, and Insurance)
- Government and Defense
- IT and Telecom
- Healthcare and Pharmaceuticals
- Energy and Utilities (Critical Infrastructure)
- Academia and Education
Value Chain Analysis For Cyber Range Market
The value chain of the Cyber Range Market begins with upstream activities focused on technology development, specifically the creation of sophisticated virtualization engines, network emulation software, and proprietary content development tools capable of rapidly generating and deploying realistic network images and simulated attack tools. Upstream providers include core technology vendors supplying virtualization layers (like hypervisors and container technology) and specialized software firms focusing on proprietary threat intelligence libraries and scenario scripting frameworks that ensure the fidelity and relevance of the training environment. Success at this stage relies heavily on intellectual property regarding network modeling and the ability to encapsulate complex, multi-layered operating systems and application stacks into reproducible, isolated environments ready for deployment.
The midstream phase involves the core platform providers who integrate these foundational technologies, package the software and services, and manage the infrastructure—whether cloud-based or on-premise—to deliver the functional cyber range solution. This phase is characterized by platform customization, integration with existing enterprise security tools (SIEM/SOAR integration), and the professional services necessary for onboarding and tailoring the range environment to the specific organizational security posture or compliance requirements of the end-user. Distribution channels are critical, primarily involving direct sales to large governmental and defense contracts requiring complex customization, and indirect sales through channel partners, Value-Added Resellers (VARs), and Managed Security Service Providers (MSSPs) who bundle CRaaS offerings into broader security service contracts, effectively extending market reach to smaller organizations.
Downstream activities focus entirely on the end-user interaction and post-deployment services. This includes content delivery, where specialized curriculum developers and security experts create high-fidelity attack scenarios and educational modules (the true value proposition). Direct engagement involves the vendor providing continuous managed services, platform maintenance, and expert mentorship during large-scale exercises. Indirect channels utilize the cyber range platform via educational institutions or third-party training organizations that leverage the technology to deliver certifications and specialized career development programs, ensuring a continuous pipeline of skilled professionals trained on the vendor’s specific range architecture, ultimately maximizing the platform’s utilization and maximizing recurring revenue streams through specialized service contracts.
Cyber Range Market Potential Customers
The primary consumers and end-users of cyber range solutions are organizations with high stakes in maintaining robust cybersecurity posture and those mandated by regulation to demonstrate verifiable security competencies. Government and Defense entities represent a foundational customer base, requiring high-fidelity, isolated ranges for training military cyber warfare units, testing critical national infrastructure defenses against nation-state attacks, and validating complex command and control systems under simulated duress. These customers typically demand highly secure, on-premise solutions with customization capabilities tailored to specific classified networks and bespoke threat intelligence models, placing emphasis on resilience and confidentiality over cost-efficiency or multi-tenancy.
Financial Services (BFSI) and IT & Telecom sectors constitute the largest commercial customer segments. BFSI firms utilize cyber ranges extensively for mandatory compliance training (e.g., simulating breaches to meet DORA or similar regulations), training incident response teams to handle complex financial fraud scenarios, and validating the security of new digital banking products before deployment. IT & Telecom providers, facing continuous threats to large-scale network infrastructures and data centers, use ranges to train network security engineers on sophisticated network intrusion detection, telecommunications infrastructure hardening, and rapid response to large-scale denial-of-service (DDoS) attacks, viewing it as essential operational expenditure to minimize system downtime and service disruption risk.
Emerging high-potential customer groups include Critical Infrastructure sectors such as Energy, Utilities, and Healthcare. These organizations are increasingly targeted due to the high impact potential of operational technology (OT) disruption. They require specialized cyber ranges capable of integrating IT and OT network simulation (e.g., simulating SCADA systems, power grids, or hospital medical devices) to train engineers on managing attacks that bridge the IT/OT divide, where physical safety and service continuity are paramount. Academic institutions and commercial training providers also represent a growing segment, leveraging CRaaS models to deliver scalable, practical cybersecurity education to students and professionals seeking industry certifications, effectively serving as indirect customers by integrating the range technology into their curriculum framework to address the global skills gap at scale.
| Report Attributes | Report Details |
|---|---|
| Market Size in 2026 | $1.8 Billion USD |
| Market Forecast in 2033 | $4.6 Billion USD |
| Growth Rate | 14.8% CAGR |
| Historical Year | 2019 to 2024 |
| Base Year | 2025 |
| Forecast Year | 2026 - 2033 |
| DRO & Impact Forces |
|
| Segments Covered |
|
| Key Companies Covered | Cyberbit, RangeForce, Keysight Technologies (Ixia), Darktrace, Palo Alto Networks, Cisco Systems, Symantec (Broadcom), L3Harris Technologies, Lockheed Martin, EWA CyberRange, Cloud Range, Circadence, SimSpace, Mandiant (Google Cloud), ECS International, Cydome, Cyber Test Systems, Fortinet, Mimecast, HackerOne |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Enquiry Before Buy | Have specific requirements? Send us your enquiry before purchase to get customized research options. Request For Enquiry Before Buy |
Cyber Range Market Key Technology Landscape
The technological core of the Cyber Range Market is built upon robust virtualization and emulation technologies, critical for creating high-fidelity, isolated network environments that precisely mirror real-world operational systems without incurring physical risk. Modern ranges extensively utilize advanced hypervisors (such as VMware ESXi, KVM) alongside cutting-edge containerization platforms (Docker, Kubernetes) to rapidly provision and tear down complex, multi-tier network topologies and diverse operating system images. This use of both virtualization and containerization enables vendors to strike a balance between high-fidelity hardware emulation (necessary for OT systems) and rapid, resource-efficient deployment of application-layer training environments. Furthermore, specialized network simulation tools are employed to accurately emulate latency, traffic congestion, and firewall behaviors, ensuring that trainees experience realistic operational challenges and network impacts during simulated attacks, critical for testing complex security stack configurations and optimizing incident response workflows within the synthetic network.
A crucial technological advancement driving the market is the deep integration of software-defined networking (SDN) principles. SDN allows cyber range platforms to dynamically reconfigure network topologies and segment attack traffic flows on the fly, enabling instructors to instantly alter scenario parameters or introduce unexpected network failures to challenge trainees dynamically. Complementary to SDN is the increasing deployment of automation and orchestration tools (often leveraging APIs and Python scripting) that manage the complex lifecycle of a training session—from the initial infrastructure spin-up and attack injection to post-exercise data capture and environment cleanup. These orchestration layers are fundamental for achieving the necessary scalability required by cloud-based Cyber Range as a Service (CRaaS) models, supporting thousands of concurrent users running highly individualized, isolated scenarios without resource contention or cross-contamination.
The emerging technological frontier involves Artificial Intelligence and Machine Learning integration. AI is being utilized in two primary ways: first, to create “smart” simulated adversaries (Adversarial AI) capable of adaptive, non-deterministic attacks that react to trainee defenses, forcing more realistic critical thinking; and second, in assessment and analytics engines. These engines use ML algorithms to analyze vast amounts of log data generated during a drill, providing objective, quantitative metrics on team performance, skill gaps, and adherence to security protocols. The blending of high-fidelity emulation, dynamic orchestration, and AI-driven intelligence is transforming cyber ranges from static labs into predictive, highly personalized, and operationally relevant readiness platforms, setting the technological benchmark for future security training investment and continuous professional development.
Regional Highlights
- North America (Dominant Market Share): North America, particularly the United States, commands the largest share of the global Cyber Range Market revenue. This dominance is attributed to substantial defense and homeland security expenditures, the presence of major technology vendors and early adopters, and stringent regulatory environments (e.g., NIST, critical infrastructure mandates) compelling organizations in the BFSI and IT sectors to invest heavily in advanced simulation and testing capabilities. High spending on R&D for cutting-edge cyber warfare technologies and robust academic partnerships also contribute to maintaining market leadership, focusing on integrating next-generation AI and quantum security training modules.
- Europe (Steady Growth and Regulatory Driver): The European market is expanding steadily, driven primarily by the need for compliance with comprehensive data privacy regulations like the GDPR and emerging directives such as NIS 2, which emphasize verifiable cybersecurity preparedness across critical sectors. Governments across the EU are actively investing in national cyber centers and military cyber ranges to standardize defense capabilities. The market here shows a strong preference for cloud-based CRaaS solutions that offer accessibility for multinational corporations operating across various member states, with key growth concentrated in the UK, Germany, and France.
- Asia Pacific (Highest Projected CAGR): APAC is expected to demonstrate the highest Compound Annual Growth Rate due to rapid digital transformation across emerging economies (India, Southeast Asia), coupled with increasing geopolitical tensions and resulting heightened awareness of cyber espionage threats. Significant government investment in national cybersecurity strategies, particularly in China, South Korea, and Singapore, aimed at bridging the professional skills gap and enhancing military capabilities, is propelling the massive adoption of cyber range platforms, moving swiftly toward highly localized and customized threat content relevant to regional adversaries.
- Latin America (Emerging Adoption): The Latin American market remains nascent but shows promise, driven by increasing foreign direct investment in technology and rising threats targeting critical financial services infrastructure. Adoption is primarily focused in Brazil and Mexico, where large organizations are beginning to allocate dedicated budgets toward formalizing cybersecurity training and utilizing cloud-based ranges to overcome limitations in local physical infrastructure and high capital costs, slowly moving away from basic theoretical training.
- Middle East and Africa (Strategic Investments): The MEA region is characterized by high, strategic investments, particularly in the Gulf Cooperation Council (GCC) states (UAE, Saudi Arabia). These investments are often state-backed, targeting national defense capabilities, oil and gas infrastructure protection (OT/ICS focus), and developing sovereign cyber defense capabilities. The emphasis is on building local talent pools quickly, resulting in demand for comprehensive platforms integrated with academic curriculum development and large-scale national cyber competition initiatives.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Cyber Range Market.- Cyberbit
- RangeForce
- Keysight Technologies (Ixia)
- Darktrace
- Palo Alto Networks
- Cisco Systems
- Symantec (Broadcom)
- L3Harris Technologies
- Lockheed Martin
- EWA CyberRange
- Cloud Range
- Circadence
- SimSpace
- Mandiant (Google Cloud)
- ECS International
- Cydome
- Cyber Test Systems
- Fortinet
- Mimecast
- HackerOne
- Raytheon Technologies
- General Dynamics IT (GDIT)
- KnowBe4
- Infosec Institute (Cengage)
- ThreatConnect
Frequently Asked Questions
Analyze common user questions about the Cyber Range market and generate a concise list of summarized FAQs reflecting key topics and concerns.What is the primary difference between a Cyber Range and standard security training simulators?
A Cyber Range offers high-fidelity, full-scope network and system emulation, allowing for hands-on, realistic incident response drills against adaptive, live attack scenarios in an isolated environment. Standard security training often relies on theoretical knowledge, virtual machine labs, or predefined, static scripts, lacking the complexity and realism necessary for true team readiness assessment against modern, sophisticated threats. Cyber ranges focus on operational capability validation, not just theoretical understanding.
How does the Cyber Range as a Service (CRaaS) model benefit Small and Medium-sized Enterprises (SMEs)?
CRaaS provides SMEs with access to highly sophisticated cyber simulation environments via the cloud on a subscription basis, eliminating the need for substantial upfront capital investment in hardware, software licensing, and specialized infrastructure staff. This model offers scalability, immediate deployment, and continuous content updates, making advanced, hands-on security training economically accessible and highly flexible for smaller security teams with limited resources and dynamic training needs.
What critical security skills gap can a Cyber Range effectively address?
Cyber ranges are specifically effective in bridging the critical skills gap related to hands-on incident handling, rapid threat hunting, collaborative red/blue teaming, and decisive decision-making under high stress. They move trainees beyond theoretical knowledge to practical execution of defense strategies, significantly improving measured response times and team communication during complex, multi-stage attacks, skills that cannot be adequately developed through classroom instruction alone.
Is the integration of Operational Technology (OT) simulation a major growth driver for the market?
Yes, the integration of OT simulation is a significant growth driver. As attacks increasingly target critical infrastructure like power grids, manufacturing plants, and utilities, specialized cyber ranges capable of simulating IT/OT convergence environments are essential. These simulations allow operators to safely practice defending Industrial Control Systems (ICS) against attacks that have real-world physical consequences, addressing a severe vulnerability gap in traditionally segregated environments and satisfying emerging regulatory mandates for resilience.
What role does Artificial Intelligence play in enhancing the effectiveness of cyber range platforms?
AI plays a dual role: enhancing realism and improving assessment. AI facilitates the creation of dynamic, adaptive adversaries (Adversarial AI) that react intelligently to defense actions, making training scenarios more challenging and relevant. Additionally, ML algorithms are used for automated performance analysis, providing instructors and trainees with objective, data-driven feedback on competencies, identifying precise skill deficiencies, and tailoring subsequent training paths automatically for optimized learning outcomes.
To check our Table of Contents, please mail us at: sales@marketresearchupdate.com
Research Methodology
The Market Research Update offers technology-driven solutions and its full integration in the research process to be skilled at every step. We use diverse assets to produce the best results for our clients. The success of a research project is completely reliant on the research process adopted by the company. Market Research Update assists its clients to recognize opportunities by examining the global market and offering economic insights. We are proud of our extensive coverage that encompasses the understanding of numerous major industry domains.
Market Research Update provide consistency in our research report, also we provide on the part of the analysis of forecast across a gamut of coverage geographies and coverage. The research teams carry out primary and secondary research to implement and design the data collection procedure. The research team then analyzes data about the latest trends and major issues in reference to each industry and country. This helps to determine the anticipated market-related procedures in the future. The company offers technology-driven solutions and its full incorporation in the research method to be skilled at each step.
The Company's Research Process Has the Following Advantages:
- Information Procurement
The step comprises the procurement of market-related information or data via different methodologies & sources.
- Information Investigation
This step comprises the mapping and investigation of all the information procured from the earlier step. It also includes the analysis of data differences observed across numerous data sources.
- Highly Authentic Source
We offer highly authentic information from numerous sources. To fulfills the client’s requirement.
- Market Formulation
This step entails the placement of data points at suitable market spaces in an effort to assume possible conclusions. Analyst viewpoint and subject matter specialist based examining the form of market sizing also plays an essential role in this step.
- Validation & Publishing of Information
Validation is a significant step in the procedure. Validation via an intricately designed procedure assists us to conclude data-points to be used for final calculations.
×
Request Free Sample:
Related Reports
Select License

Why Choose Us

We're cost-effective and Offered Best services:
We are flexible and responsive startup research firm. We adapt as your research requires change, with cost-effectiveness and highly researched report that larger companies can't match.

Information Safety
Market Research Update ensure that we deliver best reports. We care about the confidential and personal information quality, safety, of reports. We use Authorize secure payment process.

We Are Committed to Quality and Deadlines
We offer quality of reports within deadlines. We've worked hard to find the best ways to offer our customers results-oriented and process driven consulting services.

Our Remarkable Track Record
We concentrate on developing lasting and strong client relationship. At present, we hold numerous preferred relationships with industry leading firms that have relied on us constantly for their research requirements.

Best Service Assured
Buy reports from our executives that best suits your need and helps you stay ahead of the competition.

Customized Research Reports
Our research services are custom-made especially to you and your firm in order to discover practical growth recommendations and strategies. We don't stick to a one size fits all strategy. We appreciate that your business has particular research necessities.

Service Assurance
At Market Research Update, we are dedicated to offer the best probable recommendations and service to all our clients. You will be able to speak to experienced analyst who will be aware of your research requirements precisely.
Contact With Our Sales Team
Customer Testimonials
The content of the report is always up to the mark. Good to see speakers from expertise authorities.
Privacy requested , Managing Director
A lot of unique and interesting topics which are described in good manner.
Privacy requested, President
Well researched, expertise analysts, well organized, concrete and current topics delivered in time.
Privacy requested, Development Manager
