Cyber Security Tools Market Size, By Region (North America, Europe, Asia-Pacific, Latin America, Middle East and Africa), By Statistics, Trends, Outlook and Forecast 2026 to 2033 (Financial Impact Analysis)
ID : MRU_ 440203 | Date : Jan, 2026 | Pages : 241 | Region : Global | Publisher : MRU
Cyber Security Tools Market Size
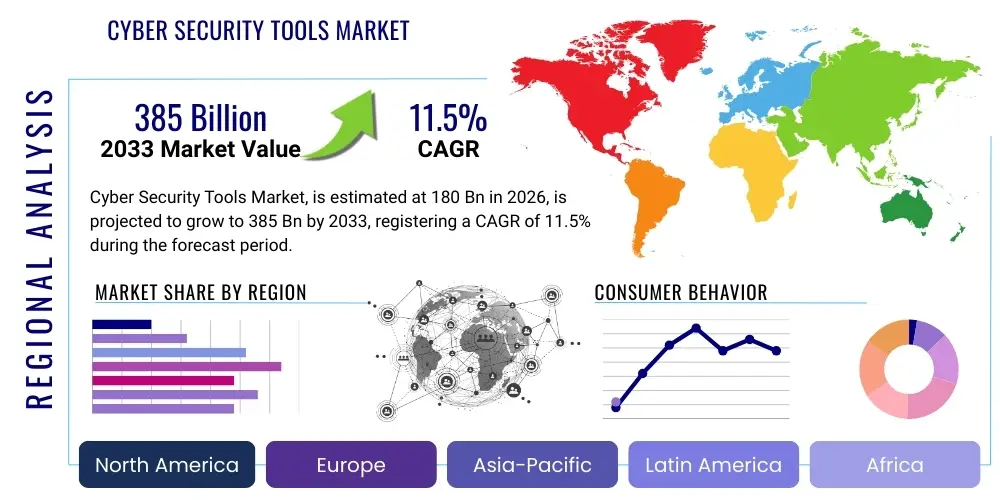
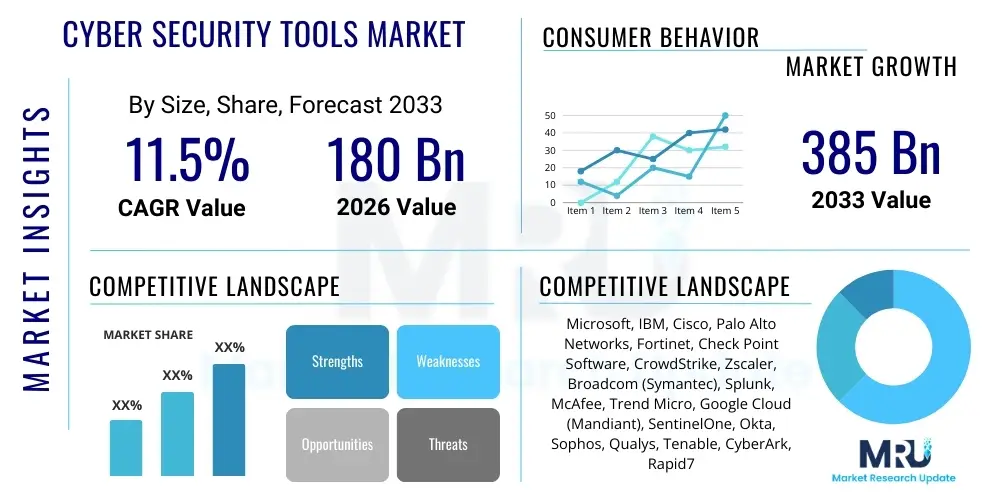
The Cyber Security Tools Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 11.5% between 2026 and 2033. The market is estimated at USD 180 Billion in 2026 and is projected to reach USD 385 Billion by the end of the forecast period in 2033. This significant growth trajectory is underpinned by the escalating sophistication and frequency of cyber threats globally, compelling organizations across all sectors to continually enhance their defensive capabilities. The increasing digitalization of business processes, coupled with the widespread adoption of cloud computing, IoT, and mobile technologies, has exponentially expanded the attack surface, thereby fueling the demand for advanced security solutions. The market’s expansion is further bolstered by a growing awareness among enterprises and governments regarding the critical importance of robust cybersecurity infrastructure to protect sensitive data, maintain operational integrity, and comply with evolving regulatory mandates.
The imperative for stringent cyber defense is no longer a discretionary expenditure but a fundamental operational requirement. Organizations are increasingly recognizing that investments in cyber security tools yield substantial returns by mitigating financial losses from breaches, safeguarding brand reputation, and ensuring business continuity. This proactive stance is driving accelerated adoption of comprehensive security suites that integrate multiple layers of protection, from endpoint to cloud environments. Furthermore, the global cybersecurity skills gap has intensified the reliance on automated and intelligent security tools that can compensate for human resource limitations, pushing innovation in areas like AI-driven threat detection and automated incident response.
Geographically, market growth is anticipated across all major regions, with North America and Europe currently holding dominant shares due to high technological adoption and stringent regulatory frameworks. However, the Asia Pacific region is expected to exhibit the fastest growth, driven by rapid economic development, digital transformation initiatives, and increasing awareness of cyber risks among businesses and consumers. Latin America, the Middle East, and Africa are also poised for substantial expansion as their digital economies mature and regulatory landscapes evolve, creating new opportunities for cybersecurity solution providers. This global demand underscores the universal challenge of cyber threats and the universal need for effective tools to combat them.
Cyber Security Tools Market introduction
The cyber security tools market encompasses a sophisticated and rapidly evolving ecosystem of technologies and services meticulously designed to safeguard digital assets, networks, and sensitive information from an ever-increasing array of sophisticated cyber threats. These tools are indispensable across virtually all sectors, ranging from critical infrastructure and financial services to healthcare and government agencies, providing multi-layered defenses against vulnerabilities and malicious attacks. The fundamental purpose of these tools is to ensure the confidentiality, integrity, and availability of data, thereby upholding operational continuity and fostering trust in the digital realm. Their application spans comprehensive solutions including threat detection, prevention, incident response, and recovery, making them foundational components of any robust organizational security posture in the contemporary digital landscape.
The product description for cyber security tools is broad, covering a spectrum from foundational antivirus and firewall solutions to advanced threat intelligence platforms, Security Information and Event Management (SIEM) systems, Intrusion Detection/Prevention Systems (IDPS), data loss prevention (DLP) tools, Identity and Access Management (IAM) solutions, and cloud security brokers. These tools are engineered to address specific vulnerabilities and attack vectors, working in concert to create a holistic security framework. For instance, endpoint detection and response (EDR) tools focus on securing individual devices, while network security tools protect the perimeter and internal traffic. The continuous innovation in this space is driven by the dynamic nature of cyber threats, requiring constant adaptation and enhancement of defensive capabilities.
Major applications of cyber security tools span enterprise-wide protection, including securing corporate networks, cloud infrastructures, mobile devices, and industrial control systems. They are crucial for protecting intellectual property, customer data, and financial transactions. Key benefits include preventing data breaches, reducing operational downtime, ensuring compliance with industry regulations like GDPR and HIPAA, and mitigating financial losses associated with cyberattacks. The market is primarily driven by the escalating volume and complexity of cyber threats, the increasing adoption of digital transformation initiatives across industries, and the stringent regulatory pressures mandating robust data protection measures. These factors collectively create a pervasive and sustained demand for advanced and integrated cyber security tools.
Cyber Security Tools Market Executive Summary
The Cyber Security Tools Market is currently experiencing robust growth, primarily fueled by an increasingly complex threat landscape and the rapid pace of digital transformation across global enterprises. Business trends indicate a significant shift towards integrated security platforms that offer comprehensive protection rather than disparate point solutions. Organizations are prioritizing Security-as-a-Service (SaaS) models and managed security services to address the persistent cybersecurity talent gap and to leverage the expertise of specialized providers. Furthermore, the convergence of IT and Operational Technology (OT) security is emerging as a critical trend, driven by the need to protect industrial control systems from cyber threats, reflecting a broader understanding of interconnected risk across diverse environments. This strategic shift underscores a mature approach to security, recognizing that isolated defenses are no longer sufficient against sophisticated adversaries.
Regional trends highlight North America and Europe as mature markets with high adoption rates, propelled by stringent regulatory frameworks and significant technological advancements. These regions are witnessing increased investments in advanced technologies like Artificial Intelligence (AI) and Machine Learning (ML) for enhanced threat detection and response capabilities. The Asia Pacific region is poised for accelerated growth, attributed to rapid industrialization, burgeoning digital economies, and a heightened awareness of cybersecurity risks among businesses and governments. Emerging markets in Latin America, the Middle East, and Africa are also showing promising growth, albeit from a lower base, as they undertake significant digital infrastructure projects and implement new data protection regulations, driving foundational and advanced security tool adoption.
Segmentation trends reveal strong performance across various solution types, with cloud security, endpoint security, and network security segments demonstrating substantial expansion due to the pervasive shift to cloud environments and the distributed nature of modern workforces. Within services, managed security services are experiencing burgeoning demand as organizations seek to offload the complexities of security operations to expert third parties. The market is also seeing increased penetration of security solutions within Small and Medium-sized Enterprises (SMEs), historically underserved, as they become more frequent targets of cyberattacks and recognize the imperative for protection. The industry vertical segment continues to see tailored solutions emerge, particularly for highly regulated sectors such as BFSI, healthcare, and government, where compliance requirements drive specialized tool adoption.
AI Impact Analysis on Cyber Security Tools Market
Common user questions related to the impact of AI on the Cyber Security Tools Market often revolve around its effectiveness in detecting novel threats, its role in automating security operations, the potential for AI-driven attacks, and the ethical implications of using AI in cybersecurity. Users frequently inquire about how AI can provide a competitive edge in threat intelligence, predict future attack vectors, and reduce the burden on human analysts. There is also significant interest in understanding the practical implementation challenges, such as the need for vast datasets for training, the risk of algorithmic bias, and the potential for 'adversarial AI' where malicious actors attempt to manipulate AI defenses. These questions collectively highlight a dual perception of AI: a powerful enabler for defense, but also a new frontier for sophisticated threats, necessitating a nuanced approach to its integration within security strategies.
The key themes emerging from user concerns include the promise of enhanced threat detection accuracy, especially for zero-day exploits and polymorphic malware, through AI's ability to analyze vast amounts of data and identify subtle patterns beyond human capabilities. Expectations are high for AI to streamline security operations, moving from reactive responses to proactive threat hunting and automated remediation, thereby freeing up valuable human resources for more complex strategic tasks. However, there are also significant concerns regarding the ability of AI systems to handle false positives and negatives effectively, the transparency of AI decision-making processes, and the ethical considerations surrounding surveillance and privacy when AI is deployed to monitor network activities. Users also worry about the escalating AI arms race between defenders and attackers, where AI could be weaponized for more potent and evasive cyberattacks.
Ultimately, users anticipate that AI will fundamentally transform the cybersecurity landscape, making security tools more intelligent, adaptive, and efficient. They expect AI to not only improve current security functions but also to enable entirely new capabilities, such as automated vulnerability management, predictive risk assessment, and personalized security postures. The desire for a more resilient and self-healing security infrastructure driven by AI is strong. However, this optimism is tempered by the recognition that AI integration requires careful planning, continuous learning, and a robust understanding of its limitations and potential misuse. The overall expectation is a significant enhancement of defensive capabilities, but with an acute awareness of the challenges and ethical responsibilities that accompany such powerful technology.
- Enhanced Threat Detection: AI algorithms rapidly analyze vast datasets to identify anomalies and indicators of compromise that human analysts might miss, improving the detection of sophisticated and zero-day threats.
- Automated Incident Response: AI-powered tools can automate aspects of incident response, such as quarantining infected systems, blocking malicious IP addresses, and patching vulnerabilities, significantly reducing response times.
- Predictive Security Analytics: AI enables predictive capabilities by learning from historical threat data to anticipate future attack patterns and proactively strengthen defenses, moving from reactive to proactive security.
- Reduced False Positives: Advanced AI and ML models can refine threat alerts, reducing the volume of false positives that can overwhelm security teams, allowing them to focus on genuine threats.
- Adaptive Security Systems: AI allows security tools to continuously learn and adapt to new threats and changes in the environment, evolving their defenses over time without constant manual intervention.
- Improved Vulnerability Management: AI can scan systems for vulnerabilities more effectively, prioritize patches based on risk assessment, and even suggest remediation strategies.
- Resource Optimization: By automating routine tasks and improving detection accuracy, AI helps optimize scarce cybersecurity human resources, allowing experts to focus on strategic initiatives.
- AI-Driven Attacks: The emergence of AI used by adversaries for more sophisticated phishing, malware generation, and automated attacks poses a new challenge for defenders.
- Data Privacy Concerns: The use of AI in monitoring and analyzing large volumes of data raises concerns about data privacy and the ethical implications of continuous surveillance.
- Skill Gap Mitigation: AI tools can augment the capabilities of less experienced security personnel, helping to bridge the global cybersecurity talent gap.
DRO & Impact Forces Of Cyber Security Tools Market
The cyber security tools market is profoundly influenced by a complex interplay of Drivers, Restraints, and Opportunities, which collectively constitute the primary Impact Forces shaping its trajectory. A fundamental driver is the relentless escalation in the volume, sophistication, and diversity of cyber threats. From state-sponsored attacks and organized cybercrime to insider threats and financially motivated ransomware campaigns, the digital landscape is perpetually under siege, necessitating continuous investment in advanced defensive tools. The rapid pace of digital transformation across industries, encompassing cloud adoption, IoT proliferation, and remote work models, has dramatically expanded the attack surface, creating new vulnerabilities that demand robust security solutions. Furthermore, a burgeoning global regulatory environment, with mandates like GDPR, CCPA, HIPAA, and various national cybersecurity frameworks, compels organizations to deploy comprehensive tools to ensure compliance and avoid severe penalties, thus acting as a significant market stimulant.
Despite these powerful drivers, several significant restraints impede market growth. The high initial investment and ongoing operational costs associated with implementing and maintaining sophisticated cyber security tools can be prohibitive for many organizations, particularly Small and Medium-sized Enterprises (SMEs) with limited budgets. The pervasive global shortage of skilled cybersecurity professionals is another major restraint, as even the most advanced tools require expert deployment, configuration, and monitoring to be effective. This talent gap often leads to organizations struggling to fully leverage their security investments or leaving security gaps unaddressed. Moreover, the inherent complexity of integrating diverse security tools from multiple vendors, often resulting in fragmented security postures and management overhead, poses a considerable challenge for enterprises striving for a unified defense strategy.
Amidst these challenges, significant opportunities abound within the cyber security tools market. The burgeoning integration of Artificial Intelligence (AI) and Machine Learning (ML) offers a transformative opportunity to enhance threat detection, automate response, and provide predictive insights, moving security from a reactive to a proactive paradigm. The rapid expansion of cloud computing presents a substantial opportunity for cloud-native security solutions, secure access service edge (SASE) platforms, and cloud security posture management (CSPM) tools as enterprises migrate their operations to the cloud. Furthermore, the growing demand for managed security services (MSS) and Security-as-a-Service (SaaS) models provides an avenue for vendors to offer comprehensive solutions to organizations lacking in-house expertise or resources. The emergence of specialized solutions for protecting critical infrastructure, IoT devices, and industrial control systems (ICS) also represents lucrative niches, capitalizing on new vectors of vulnerability as these technologies become more integrated into daily operations. The evolving landscape of threats and technologies continuously generates new avenues for innovation and market expansion, provided vendors can overcome the existing restraints and capitalize on these emerging trends.
Segmentation Analysis
The Cyber Security Tools Market is meticulously segmented to provide granular insights into its diverse components and evolving dynamics. This segmentation typically dissects the market based on Solution Type, Service, Deployment Model, Organization Size, and Industry Vertical, each revealing distinct growth patterns and competitive landscapes. Understanding these segments is critical for both market participants and potential investors, as it highlights areas of high growth, specific pain points, and emerging opportunities. The comprehensive nature of cybersecurity means that different tools and services cater to varying needs, from securing individual endpoints to protecting vast cloud infrastructures, influencing purchasing decisions and deployment strategies across organizations of all sizes and sectors. This structured approach allows for a clearer analysis of market demand and supply across the intricate cybersecurity ecosystem.
The Solution Type segment, for instance, reflects the specific security functionalities offered, such as network security, endpoint security, cloud security, and data security. Each of these sub-segments addresses particular attack vectors and vulnerabilities, driving specialized product development and market competition. Service segmentation, on the other hand, distinguishes between professional services like consulting and implementation, and managed security services, where third-party providers handle ongoing security operations. The growing complexity of threats and the shortage of in-house expertise are increasingly driving demand for managed services. The Deployment Model segment differentiates between on-premise solutions, favored by organizations with strict data control requirements, and cloud-based solutions, which offer flexibility, scalability, and often a lower total cost of ownership, aligning with modern IT infrastructure trends.
Organization Size segmentation categorizes demand from Small and Medium-sized Enterprises (SMEs) versus Large Enterprises, acknowledging their differing budgets, security needs, and resource availability. SMEs, once considered less attractive targets, are now increasingly vulnerable, driving growth in accessible, scalable security solutions. Finally, the Industry Vertical segmentation recognizes the unique compliance requirements, threat profiles, and data sensitivity levels across sectors such as Banking, Financial Services, and Insurance (BFSI), IT & Telecommunications, Healthcare, Government, and Manufacturing. This allows vendors to tailor their offerings and go-to-market strategies to meet the specific demands of each industry, ensuring relevance and effectiveness of their cybersecurity tool portfolios in a highly specialized market.
- By Solution Type:
- Network Security (Firewalls, IDS/IPS, VPN, Network Access Control)
- Endpoint Security (Antivirus, EDR, Mobile Security)
- Cloud Security (CASB, CWPP, CSPM, Cloud IAM)
- Application Security (WAF, SAST, DAST, RASP)
- Data Security (DLP, Encryption, Tokenization, Database Security)
- Identity and Access Management (IAM)
- Security Information and Event Management (SIEM)
- Security Orchestration, Automation, and Response (SOAR)
- Vulnerability Management
- Threat Intelligence
- Unified Threat Management (UTM)
- By Service:
- Professional Services (Consulting, Integration, Training & Education, Support & Maintenance)
- Managed Security Services (Managed Detection and Response - MDR, Managed SIEM, Managed Firewall)
- By Deployment Model:
- On-Premise
- Cloud (SaaS, IaaS, PaaS)
- Hybrid
- By Organization Size:
- Small and Medium-sized Enterprises (SMEs)
- Large Enterprises
- By Industry Vertical:
- Banking, Financial Services, and Insurance (BFSI)
- IT and Telecommunications
- Government and Defense
- Healthcare
- Retail and E-commerce
- Manufacturing
- Energy and Utilities
- Education
- Others
Value Chain Analysis For Cyber Security Tools Market
The value chain for the Cyber Security Tools Market is a complex and multi-faceted ecosystem that involves various stakeholders, each contributing to the delivery and consumption of cybersecurity solutions. It typically begins with upstream activities, encompassing research and development by security vendors, where new threats are analyzed, and innovative technologies are conceptualized and built. This stage involves significant investment in talent, intellectual property, and cutting-edge computational resources to create the foundational security products and platforms. These foundational elements include core security engines, artificial intelligence algorithms for threat detection, encryption protocols, and vulnerability assessment frameworks. The efficacy and innovativeness at this stage directly influence the competitive advantage and market relevance of the cybersecurity solutions downstream. Upstream suppliers also include hardware manufacturers providing secure servers and network equipment, as well as software developers creating specialized components for security applications.
Moving downstream, the value chain involves the manufacturing and integration of these developed security products and services. This includes packaging software, integrating various security modules into comprehensive suites, and developing user interfaces for management. For managed security service providers (MSSPs), this stage involves building their security operations centers (SOCs), establishing threat intelligence feeds, and developing the expertise to monitor and respond to incidents on behalf of clients. Distribution channels play a critical role in bringing these products and services to end-users. Direct sales involve vendors selling directly to large enterprises or government agencies, often through dedicated sales teams and highly customized solutions. This channel allows for direct relationship management and tailored offerings but requires significant investment in sales infrastructure.
Conversely, indirect distribution channels are highly prevalent and essential for market reach, particularly for SMEs and a broader customer base. These channels include a network of value-added resellers (VARs), system integrators, managed service providers (MSPs), and distributors. VARs add value by bundling security tools with other IT services, offering installation, configuration, and ongoing support. System integrators combine various security products with existing IT infrastructure to create holistic security solutions tailored to specific organizational needs. MSPs and MSSPs provide cybersecurity as a service, managing and monitoring security for their clients, which is especially attractive to organizations lacking in-house cybersecurity expertise. This multi-channel approach ensures that cyber security tools reach diverse end-users through partners who can provide localized support, specialized integration, and ongoing managed services, effectively bridging the gap between sophisticated security technologies and varied customer requirements.
Cyber Security Tools Market Potential Customers
The potential customers for the Cyber Security Tools Market are incredibly diverse, spanning virtually every sector and organization size, reflecting the universal need for robust digital protection in an interconnected world. Primarily, large enterprises across all industries constitute a significant segment of end-users. These include global corporations in finance (BFSI), technology (IT & Telecom), healthcare, manufacturing, retail, and energy. Large enterprises typically have complex IT infrastructures, massive volumes of sensitive data, and extensive regulatory compliance requirements, necessitating comprehensive and multi-layered security solutions. Their demand often includes advanced threat intelligence, Security Information and Event Management (SIEM) systems, sophisticated endpoint detection and response (EDR), and robust cloud security platforms, often deployed with a preference for on-premise or hybrid models to maintain data control and address stringent compliance needs.
Small and Medium-sized Enterprises (SMEs) represent another rapidly growing segment of potential customers. Historically underserved, SMEs are increasingly recognizing their vulnerability to cyberattacks and the severe consequences of breaches, driving their adoption of more accessible and scalable cybersecurity tools. Their needs often lean towards simpler, integrated, and cost-effective solutions, frequently delivered via cloud-based Security-as-a-Service (SaaS) models or through managed security service providers (MSSPs) due to limited in-house IT and cybersecurity expertise and budget constraints. They require protection for their endpoints, networks, and cloud applications, with a focus on ease of deployment, automated management, and compliance with general data protection regulations relevant to their operations. The increasing targeting of SMEs by cybercriminals, often as entry points to larger supply chains, has significantly heightened their demand for foundational and proactive security measures.
Beyond the corporate sector, government agencies and public sector organizations are substantial buyers of cyber security tools, driven by national security imperatives, the protection of critical infrastructure, and citizen data privacy. These entities often require highly specialized and certified solutions for data encryption, secure communications, and robust perimeter defense. Additionally, individual consumers, while not always directly purchasing enterprise-grade tools, contribute to the market through antivirus software, VPN services, and identity theft protection, highlighting the pervasive reach of cybersecurity needs. Emerging areas like industrial control systems (ICS) and operational technology (OT) in manufacturing, energy, and utilities are also becoming critical customers, demanding specialized security solutions to protect physical assets and processes from cyber threats, illustrating the expanding definition of 'digital assets' requiring protection.
| Report Attributes | Report Details |
|---|---|
| Market Size in 2026 | USD 180 Billion |
| Market Forecast in 2033 | USD 385 Billion |
| Growth Rate | 11.5% CAGR |
| Historical Year | 2019 to 2024 |
| Base Year | 2025 |
| Forecast Year | 2026 - 2033 |
| DRO & Impact Forces |
|
| Segments Covered |
|
| Key Companies Covered | Microsoft, IBM, Cisco, Palo Alto Networks, Fortinet, Check Point Software, CrowdStrike, Zscaler, Broadcom (Symantec), Splunk, McAfee, Trend Micro, Google Cloud (Mandiant), SentinelOne, Okta, Sophos, Qualys, Tenable, CyberArk, Rapid7 |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Enquiry Before Buy | Have specific requirements? Send us your enquiry before purchase to get customized research options. Request For Enquiry Before Buy |
Cyber Security Tools Market Key Technology Landscape
The Cyber Security Tools market is characterized by a dynamic and continually evolving technology landscape, driven by the need to counter increasingly sophisticated cyber threats and adapt to new IT paradigms. A foundational technology remains the widespread use of encryption, which secures data both in transit and at rest, forming the backbone of privacy and integrity. Firewall and Intrusion Detection/Prevention Systems (IDPS) continue to evolve, incorporating advanced packet inspection and behavioral analysis to detect and block malicious traffic more effectively. The shift towards cloud computing has given rise to a suite of cloud-native security technologies, including Cloud Access Security Brokers (CASB) for monitoring cloud application usage, Cloud Workload Protection Platforms (CWPP) for securing virtual machines and containers, and Cloud Security Posture Management (CSPM) for ensuring compliance and identifying misconfigurations in cloud environments.
The integration of Artificial Intelligence (AI) and Machine Learning (ML) is rapidly transforming the market, moving beyond signature-based detection to advanced anomaly detection, predictive analytics, and automated threat response. AI/ML algorithms power next-generation antivirus (NGAV), Endpoint Detection and Response (EDR) solutions, and Security Information and Event Management (SIEM) platforms, enabling them to identify novel threats, analyze vast amounts of security data, and reduce false positives. Another critical technology is Identity and Access Management (IAM), which includes multi-factor authentication (MFA), single sign-on (SSO), and privileged access management (PAM), all crucial for controlling who has access to what resources and preventing unauthorized access. These technologies are foundational for zero-trust architectures, where no user or device is trusted by default, regardless of their location inside or outside the network perimeter.
Furthermore, Security Orchestration, Automation, and Response (SOAR) platforms are gaining prominence, designed to automate repetitive security tasks, streamline incident response workflows, and integrate various security tools into a cohesive system. This significantly enhances the efficiency and effectiveness of Security Operations Centers (SOCs). Behavioral analytics, leveraging machine learning, is also becoming paramount for detecting user and entity behavioral anomalies (UEBA) that may indicate insider threats or compromised accounts. The adoption of blockchain technology is being explored for secure identity management and immutable logging, offering new avenues for enhancing data integrity and trust. Lastly, advanced threat intelligence platforms, often enriched with AI, provide real-time insights into emerging threats, attacker tactics, and vulnerabilities, enabling proactive defense strategies. These technologies collectively form a robust and adaptive defense ecosystem, constantly evolving to meet the challenges posed by the ever-changing cyber threat landscape.
Regional Highlights
- North America: North America, particularly the United States and Canada, stands as a dominant force in the Cyber Security Tools Market. This leadership is attributed to several key factors, including a highly advanced technological infrastructure, a proactive approach to cybersecurity regulations, and a significant presence of both established cybersecurity vendors and innovative startups. The region's extensive adoption of cloud services, IoT, and mobile technologies by large enterprises and government agencies creates a vast attack surface, driving continuous investment in sophisticated security solutions. Additionally, stringent regulatory frameworks such as HIPAA, GLBA, and various state-specific data breach notification laws compel organizations to deploy robust security tools to ensure compliance and protect sensitive data. The strong venture capital funding ecosystem also supports rapid innovation, fostering a competitive market landscape with a high demand for cutting-edge solutions, including AI-driven threat intelligence and advanced endpoint protection.
- Europe: Europe represents another mature and substantial market for cyber security tools, characterized by a complex regulatory environment and a strong emphasis on data privacy. The General Data Protection Regulation (GDPR) has profoundly influenced cybersecurity investments across the continent, mandating stringent data protection measures and driving demand for data loss prevention (DLP), encryption, and robust identity and access management (IAM) solutions. Countries like the UK, Germany, France, and the Nordics are at the forefront of cybersecurity adoption, with significant government initiatives aimed at strengthening national cyber defenses and critical infrastructure protection. The region's diverse economic landscape, encompassing strong manufacturing, financial services, and IT sectors, ensures a broad and sustained demand for a wide range of security tools. The increasing focus on supply chain security and the rising frequency of ransomware attacks further accelerate market growth across European nations, prompting organizations to adopt comprehensive security frameworks.
- Asia Pacific (APAC): The Asia Pacific region is poised for the fastest growth in the Cyber Security Tools Market, driven by rapid digital transformation, burgeoning economies, and a growing awareness of cyber risks. Countries such as China, India, Japan, Australia, and South Korea are experiencing massive investments in digital infrastructure, cloud computing, and smart city initiatives, which inherently increase their vulnerability to cyber threats. This expansion creates an enormous greenfield opportunity for cybersecurity vendors. While regulatory frameworks are still evolving in some parts of the region, countries like Australia and Singapore have established advanced cybersecurity policies that serve as benchmarks. The rise of e-commerce, mobile banking, and digital payments across APAC also fuels demand for application security, data security, and fraud prevention tools. As businesses in the region scale digitally, the adoption of managed security services and cloud-based solutions is accelerating to address the twin challenges of complexity and the regional cybersecurity talent gap.
- Latin America: The Latin American market for cyber security tools is experiencing steady growth, driven by increasing internet penetration, digital commerce expansion, and an uptick in cybercrime activities. Countries like Brazil, Mexico, and Argentina are leading the adoption of cybersecurity solutions, particularly in the BFSI and telecommunications sectors. The region faces unique challenges, including a relatively nascent regulatory environment compared to North America or Europe, and a strong preference for cost-effective solutions. However, the growing recognition among local businesses and governments of the economic impact of cyberattacks is catalyzing investment in foundational security tools such as firewalls, endpoint protection, and basic identity management. The shift towards cloud computing and mobile technologies is also creating new demand for cloud security and secure access solutions. Partnerships with global cybersecurity vendors and managed security service providers are crucial for addressing the existing knowledge and resource gaps in the region.
- Middle East and Africa (MEA): The Middle East and Africa region presents a significant, albeit diverse, growth opportunity for the Cyber Security Tools Market. Countries in the Middle East, particularly the UAE and Saudi Arabia, are making substantial investments in digital transformation as part of their national visions (e.g., Vision 2030), leading to a surge in demand for advanced cybersecurity solutions to protect critical national infrastructure, smart cities, and growing digital economies. High-profile cyberattacks and geopolitical considerations also drive significant government and enterprise spending on robust defensive capabilities. In Africa, while the market is still developing, rapid mobile penetration, increased digital banking, and emerging regulatory frameworks are creating a growing need for foundational security tools. Challenges such as limited budgets, lack of skilled personnel, and fragmented digital infrastructures exist, but are gradually being overcome by a growing understanding of cyber risks and strategic partnerships. The demand for managed security services and cloud-based solutions is particularly strong across the MEA region, offering scalable and accessible protection.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Cyber Security Tools Market.- Microsoft
- IBM
- Cisco
- Palo Alto Networks
- Fortinet
- Check Point Software Technologies
- CrowdStrike
- Zscaler
- Broadcom (Symantec)
- Splunk
- McAfee
- Trend Micro
- Google Cloud (Mandiant)
- SentinelOne
- Okta
- Sophos
- Qualys
- Tenable
- CyberArk
- Rapid7
Frequently Asked Questions
Analyze common user questions about the Cyber Security Tools market and generate a concise list of summarized FAQs reflecting key topics and concerns.What is the current growth rate of the Cyber Security Tools Market?
The Cyber Security Tools Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 11.5% between 2026 and 2033, driven by escalating cyber threats and digital transformation.
How does AI impact the Cyber Security Tools Market?
AI significantly impacts the market by enhancing threat detection, enabling automated incident response, providing predictive security analytics, and optimizing resource utilization, though it also introduces new challenges like AI-driven attacks.
What are the primary drivers for the Cyber Security Tools Market?
Key drivers include the escalating volume and sophistication of cyber threats, the rapid pace of digital transformation across industries, and the increasing stringency of global cybersecurity regulations and compliance mandates.
Which regions are leading the adoption of Cyber Security Tools?
North America and Europe currently dominate the market due to mature technological infrastructures and stringent regulations, while the Asia Pacific region is expected to exhibit the fastest growth.
What are the main types of Cyber Security Tools available?
The market offers a broad range of tools including Network Security, Endpoint Security, Cloud Security, Application Security, Data Security, Identity and Access Management (IAM), and Security Information and Event Management (SIEM) solutions.
To check our Table of Contents, please mail us at: sales@marketresearchupdate.com
Research Methodology
The Market Research Update offers technology-driven solutions and its full integration in the research process to be skilled at every step. We use diverse assets to produce the best results for our clients. The success of a research project is completely reliant on the research process adopted by the company. Market Research Update assists its clients to recognize opportunities by examining the global market and offering economic insights. We are proud of our extensive coverage that encompasses the understanding of numerous major industry domains.
Market Research Update provide consistency in our research report, also we provide on the part of the analysis of forecast across a gamut of coverage geographies and coverage. The research teams carry out primary and secondary research to implement and design the data collection procedure. The research team then analyzes data about the latest trends and major issues in reference to each industry and country. This helps to determine the anticipated market-related procedures in the future. The company offers technology-driven solutions and its full incorporation in the research method to be skilled at each step.
The Company's Research Process Has the Following Advantages:
- Information Procurement
The step comprises the procurement of market-related information or data via different methodologies & sources.
- Information Investigation
This step comprises the mapping and investigation of all the information procured from the earlier step. It also includes the analysis of data differences observed across numerous data sources.
- Highly Authentic Source
We offer highly authentic information from numerous sources. To fulfills the client’s requirement.
- Market Formulation
This step entails the placement of data points at suitable market spaces in an effort to assume possible conclusions. Analyst viewpoint and subject matter specialist based examining the form of market sizing also plays an essential role in this step.
- Validation & Publishing of Information
Validation is a significant step in the procedure. Validation via an intricately designed procedure assists us to conclude data-points to be used for final calculations.
×
Request Free Sample:
Related Reports
Select License

Why Choose Us

We're cost-effective and Offered Best services:
We are flexible and responsive startup research firm. We adapt as your research requires change, with cost-effectiveness and highly researched report that larger companies can't match.

Information Safety
Market Research Update ensure that we deliver best reports. We care about the confidential and personal information quality, safety, of reports. We use Authorize secure payment process.

We Are Committed to Quality and Deadlines
We offer quality of reports within deadlines. We've worked hard to find the best ways to offer our customers results-oriented and process driven consulting services.

Our Remarkable Track Record
We concentrate on developing lasting and strong client relationship. At present, we hold numerous preferred relationships with industry leading firms that have relied on us constantly for their research requirements.

Best Service Assured
Buy reports from our executives that best suits your need and helps you stay ahead of the competition.

Customized Research Reports
Our research services are custom-made especially to you and your firm in order to discover practical growth recommendations and strategies. We don't stick to a one size fits all strategy. We appreciate that your business has particular research necessities.

Service Assurance
At Market Research Update, we are dedicated to offer the best probable recommendations and service to all our clients. You will be able to speak to experienced analyst who will be aware of your research requirements precisely.
Contact With Our Sales Team
Customer Testimonials
The content of the report is always up to the mark. Good to see speakers from expertise authorities.
Privacy requested , Managing Director
A lot of unique and interesting topics which are described in good manner.
Privacy requested, President
Well researched, expertise analysts, well organized, concrete and current topics delivered in time.
Privacy requested, Development Manager