Network Access Control Market Size By Region (North America, Europe, Asia-Pacific, Latin America, Middle East and Africa), By Statistics, Trends, Outlook and Forecast 2025 to 2032 (Financial Impact Analysis)
ID : MRU_ 428225 | Date : Oct, 2025 | Pages : 251 | Region : Global | Publisher : MRU
Network Access Control Market Size
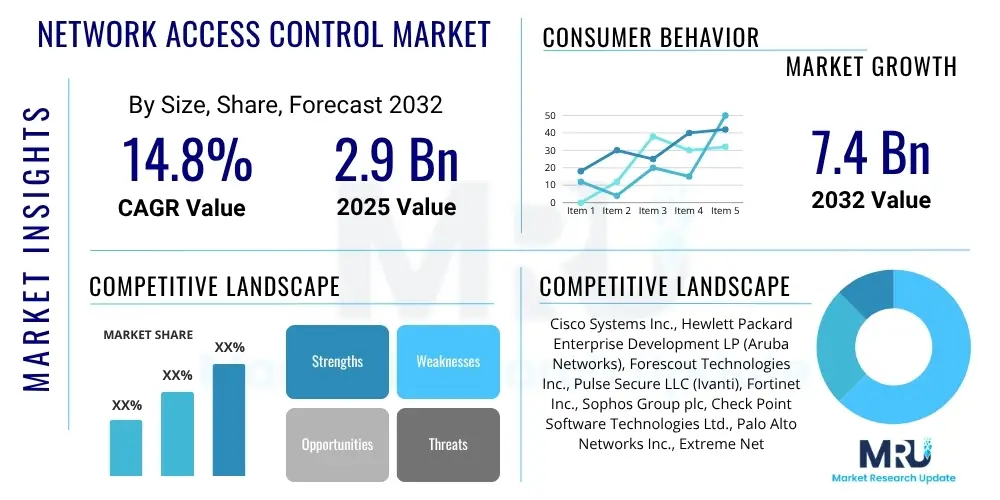
The Network Access Control Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 14.8% between 2025 and 2032. The market is estimated at USD 2.9 Billion in 2025 and is projected to reach USD 7.4 Billion by the end of the forecast period in 2032. This substantial growth is driven by the escalating need for robust cybersecurity solutions capable of managing and securing an increasingly complex and distributed network environment. Organizations across various sectors are recognizing the critical importance of controlling who and what can access their networks to prevent unauthorized data breaches and maintain operational integrity.
The expansion is further fueled by the proliferation of IoT devices, the widespread adoption of bring-your-own-device (BYOD) policies, and the continuing shift towards hybrid work models, all of which introduce new vulnerabilities and expand the attack surface. As businesses contend with sophisticated cyber threats and stringent regulatory requirements, the demand for comprehensive NAC solutions that offer granular visibility and control over network endpoints becomes paramount. The market's trajectory reflects a fundamental shift towards proactive security postures, where access management is a cornerstone of overall cybersecurity strategy.
Network Access Control Market introduction
Network Access Control (NAC) is a critical cybersecurity solution designed to enhance network security by restricting network access to only authorized users and devices, ensuring they comply with an organization's security policies. This technology operates by authenticating users and validating device security posture before granting access, effectively acting as a gatekeeper for the corporate network. NAC solutions typically encompass features such as authentication, authorization, and accounting (AAA), endpoint compliance checks, guest access management, and policy enforcement, which collectively create a highly secure and manageable network environment. By preventing unauthorized access and isolating non-compliant devices, NAC mitigates risks associated with malware propagation, insider threats, and data exfiltration.
The major applications of NAC span across diverse industries, including Banking, Financial Services, and Insurance (BFSI), IT and Telecommunications, Healthcare, Government, Manufacturing, and Retail. In these sectors, NAC is vital for securing sensitive data, ensuring regulatory compliance, and protecting critical infrastructure from cyberattacks. Its benefits are manifold, offering enhanced visibility into network assets, automated policy enforcement, improved threat containment, and streamlined compliance reporting. NAC systems help organizations manage the complexities of modern networks, which often involve a mix of corporate-owned and personal devices, on-premise and cloud resources, and a variety of wired and wireless connections.
Key driving factors for the NAC market include the pervasive rise in cyber threats and data breaches, the growing complexity of IT environments due to cloud adoption and digital transformation initiatives, and the increasing demand for secure remote access solutions. Moreover, stringent regulatory frameworks such as GDPR, HIPAA, and PCI DSS mandate robust access control mechanisms, compelling organizations to invest in NAC technologies. The proliferation of Internet of Things (IoT) devices in corporate networks also necessitates advanced NAC capabilities to secure these often vulnerable endpoints, further propelling market growth.
Network Access Control Market Executive Summary
The Network Access Control (NAC) market is undergoing significant transformation, driven by evolving business trends centered on hybrid workforces, cloud adoption, and the exponential growth of connected devices. Enterprises are increasingly seeking NAC solutions that can seamlessly integrate with existing security infrastructures, offer granular control over access privileges, and adapt to dynamic network conditions. This shift necessitates solutions that move beyond traditional on-premise deployments to embrace cloud-native and hybrid models, providing flexibility and scalability. Business trends highlight a strong preference for NAC platforms that incorporate automation, analytics, and threat intelligence to proactively manage security postures and respond to emerging threats, emphasizing ease of management and reduction in operational overhead.
Regional trends indicate North America and Europe as dominant markets due to early adoption of advanced cybersecurity technologies, stringent regulatory environments, and the presence of major solution providers. However, the Asia Pacific (APAC) region is projected to exhibit the highest growth rate, fueled by rapid digital transformation, increasing cybersecurity investments, and growing awareness among small and medium-sized enterprises (SMEs) regarding network security. Latin America, the Middle East, and Africa (MEA) are also showing promising growth, albeit from a smaller base, driven by infrastructure development and rising internet penetration. Each region's unique threat landscape and regulatory pressures are shaping the specific demands for NAC functionalities, leading to localized solution development and deployment strategies.
Segmentation trends reveal robust growth across all major categories. The solutions segment, comprising both software and hardware, continues to hold a significant market share, with a growing emphasis on cloud-based and software-defined NAC offerings. Services, including professional and managed services, are experiencing accelerated demand as organizations seek expertise in deployment, integration, and ongoing management of complex NAC environments. By deployment, hybrid and cloud-based models are gaining traction over traditional on-premise solutions due to their scalability and reduced infrastructure costs. Large enterprises remain primary adopters, but SMEs are increasingly investing in NAC as affordable, cloud-delivered options become available. End-user industries like BFSI, IT & Telecom, and Healthcare continue to be major revenue contributors, driven by high compliance needs and critical data protection requirements.
AI Impact Analysis on Network Access Control Market
User inquiries concerning AI's impact on the Network Access Control market frequently revolve around its potential to enhance threat detection, automate policy enforcement, and improve overall operational efficiency. Common questions explore how AI and Machine Learning (ML) can move NAC from a reactive to a proactive security stance, enabling predictive analytics for anomalous behavior and adaptive policy adjustments. Users are keen to understand if AI can significantly reduce false positives, accurately identify unknown threats, and simplify the management of increasingly complex network environments. There is also considerable interest in AI's role in personalizing access policies based on user behavior and device context, ultimately providing more dynamic and intelligent access control mechanisms that can keep pace with sophisticated cyberattacks.
The integration of AI into NAC solutions is fundamentally transforming how organizations manage network access and enforce security policies. AI/ML algorithms excel at processing vast amounts of network data, identifying subtle patterns, and detecting deviations from normal behavior that human analysts might miss. This capability allows NAC systems to make more informed decisions regarding access requests, recognizing malicious activities or non-compliant devices in real-time. For instance, AI can learn baseline user and device profiles, flagging any unusual login attempts, access patterns, or device configurations as potential threats, thereby improving the accuracy and speed of threat identification and response. This proactive identification is crucial in an era where cyberattacks are becoming increasingly sophisticated and stealthy.
Furthermore, AI-powered NAC solutions offer significant advancements in automating policy generation and enforcement. Instead of static, manually configured rules, AI can enable adaptive policies that dynamically adjust based on continuous risk assessments. This means that access privileges can automatically be downgraded or revoked if a device exhibits suspicious behavior or its security posture deteriorates. AI also plays a vital role in reducing the burden on IT security teams by automating routine tasks, such as classifying devices, updating compliance checks, and responding to minor policy violations. This automation not only frees up valuable human resources but also ensures more consistent and immediate policy enforcement, leading to a more resilient and efficient network security infrastructure.
- Enhanced Anomaly Detection: AI/ML algorithms analyze network traffic and user behavior patterns to detect deviations from the norm, indicating potential threats or policy violations.
- Predictive Threat Intelligence: AI helps NAC systems anticipate potential threats by correlating vast amounts of global threat data with internal network activities.
- Automated Policy Adaptation: Policies can dynamically adjust based on real-time risk assessments and learned behavioral patterns, offering adaptive access control.
- Reduced False Positives: AI improves the accuracy of threat identification, minimizing legitimate users or devices being incorrectly flagged.
- Contextual Access Decisions: AI enables more granular access control by considering multiple contextual factors like user role, device health, location, and time of access.
- Operational Efficiency: Automation of device profiling, compliance checks, and incident response reduces manual effort and improves response times.
- Zero Trust Implementation: AI supports Zero Trust architectures by continuously verifying every access attempt and assessing trust levels.
- IoT Security Augmentation: AI enhances the ability of NAC to identify, profile, and secure the vast and diverse landscape of IoT devices effectively.
DRO & Impact Forces Of Network Access Control Market
The Network Access Control market is propelled by a confluence of powerful drivers that underscore its increasing indispensability in modern cybersecurity strategies. A primary driver is the pervasive and escalating threat landscape, characterized by sophisticated malware, ransomware, and targeted attacks that necessitate robust mechanisms for controlling network access and preventing unauthorized infiltration. Coupled with this, the rapid adoption of cloud computing, the proliferation of Internet of Things (IoT) devices, and the widespread implementation of bring-your-own-device (BYOD) policies have dramatically expanded network perimeters, creating complex ecosystems that are difficult to secure without granular access control. Furthermore, stringent regulatory compliance mandates, such as GDPR, HIPAA, and PCI DSS, compel organizations to implement NAC solutions to protect sensitive data and avoid hefty penalties.
Despite these strong drivers, the NAC market faces several restraints that could impede its growth. The primary challenges include the inherent complexity of deploying and managing comprehensive NAC solutions, particularly in large, heterogeneous IT environments with legacy systems. Initial implementation costs can be significant, encompassing not only software and hardware but also professional services for integration and customization, which can be prohibitive for small and medium-sized enterprises (SMEs). Additionally, concerns regarding potential disruptions to network operations during deployment or due to misconfigured policies can create apprehension among prospective adopters. The integration of NAC with other existing security tools and IT infrastructure often presents technical hurdles, requiring specialized expertise and considerable time investments.
Opportunities within the NAC market are vast and evolving, primarily driven by technological advancements and unmet security needs. The emergence of cloud-native and software-defined NAC solutions offers greater flexibility, scalability, and reduced infrastructure overhead, making advanced access control accessible to a broader range of organizations. The integration of artificial intelligence (AI) and machine learning (ML) promises to enhance NAC capabilities through predictive analytics, automated policy enforcement, and improved anomaly detection, moving towards truly adaptive security. Furthermore, the growing demand for managed NAC services presents a significant opportunity for security service providers to offer expertise and outsource the complexities of NAC management. Expansion into operational technology (OT) and industrial IoT (IIoT) environments also represents a burgeoning frontier for NAC solutions, given the critical nature of these infrastructures.
The market is also shaped by several impact forces. Technological advancements, particularly in areas like AI, cloud computing, and advanced authentication methods, continuously redefine the capabilities and expectations for NAC solutions. The evolving threat landscape, characterized by zero-day exploits and highly targeted attacks, persistently drives the demand for more intelligent and adaptive access control. Regulatory and compliance pressures remain a significant external force, compelling organizations across all sectors to invest in NAC to avoid legal repercussions and maintain data integrity. Lastly, economic conditions and geopolitical factors can influence cybersecurity spending, affecting investment decisions in NAC technologies, though the essential nature of network security tends to maintain a baseline demand even during economic downturns.
Segmentation Analysis
The Network Access Control market is comprehensively segmented to address the diverse needs of organizations across various operational contexts and industry verticals. This segmentation allows for a detailed understanding of market dynamics, growth drivers, and specific challenges within each category, providing valuable insights for both solution providers and end-users. The market can be dissected based on component type, deployment model, organization size, and end-user industry, reflecting the varied requirements for securing network access in different environments. This granular view helps in identifying market niches and tailoring solutions that offer optimal security posture and operational efficiency.
- By Component
- Solutions (Software, Hardware)
- Services (Professional Services, Managed Services)
- By Deployment
- On-premise
- Cloud
- Hybrid
- By Organization Size
- Small and Medium-sized Enterprises (SMEs)
- Large Enterprises
- By End-User Industry
- Banking, Financial Services, and Insurance (BFSI)
- IT & Telecommunications
- Healthcare
- Government & Public Sector
- Manufacturing
- Retail & E-commerce
- Education
- Others (Utilities, Media & Entertainment)
Value Chain Analysis For Network Access Control Market
The value chain for the Network Access Control (NAC) market begins with upstream activities centered on research and development (R&D) and technology innovation. This phase involves security researchers, software developers, and hardware manufacturers who create the foundational technologies, algorithms, and components that power NAC solutions. Key activities here include developing advanced authentication protocols, endpoint profiling techniques, policy enforcement engines, and integration capabilities with other security ecosystems. Upstream suppliers include semiconductor manufacturers for hardware appliances, operating system providers, and open-source software communities that contribute to the underlying technological framework. This phase is crucial for ensuring that NAC solutions remain at the cutting edge of cybersecurity defense.
Moving downstream, the value chain encompasses the development, manufacturing, and distribution of NAC products and services. Software vendors develop comprehensive NAC platforms, often integrating third-party security intelligence feeds and cloud services. Hardware manufacturers produce dedicated NAC appliances that can enforce policies at the network edge. The distribution channel is multifaceted, including direct sales from vendors to large enterprises, indirect sales through value-added resellers (VARs), system integrators (SIs), and managed security service providers (MSSPs). These partners play a critical role in customizing solutions for specific client needs, providing implementation support, and offering ongoing maintenance and managed services, thereby extending the reach and impact of NAC solutions.
Direct channels involve vendors selling directly to end-user organizations, particularly large enterprises that have the internal expertise and resources to deploy and manage complex security solutions. This allows for direct communication, custom agreements, and specialized support. Indirect channels, on the other hand, leverage a network of partners who bring local market knowledge, specialized integration skills, and access to a broader customer base, especially SMEs. MSSPs are particularly significant as they bundle NAC with other security offerings, providing a holistic security-as-a-service model. Both direct and indirect distribution strategies are essential for market penetration, ensuring that NAC solutions reach a diverse array of customers with varying technical capabilities and budget constraints. This robust distribution network ensures that NAC technologies are effectively delivered, implemented, and supported across the global market.
Network Access Control Market Potential Customers
The Network Access Control market serves a broad and diverse range of potential customers across virtually all industry verticals, reflecting the universal need for robust network security. End-users and buyers of NAC solutions are primarily organizations seeking to secure their digital assets, comply with regulatory mandates, and protect against unauthorized network access. Large enterprises, with their expansive networks, numerous employees, and critical data, constitute a significant segment of potential customers. These organizations often face complex security challenges due to diverse IT infrastructure, hybrid cloud environments, and a high volume of connected devices, making comprehensive NAC solutions indispensable for maintaining a strong security posture.
Small and Medium-sized Enterprises (SMEs) also represent a growing segment of potential customers. While traditionally lagging in cybersecurity investments due to budget and resource constraints, SMEs are increasingly targeted by cybercriminals and are recognizing the critical importance of network access control. The availability of more affordable, cloud-based, and managed NAC services is making these solutions more accessible to smaller organizations, enabling them to achieve enterprise-grade security without significant upfront investment or in-house expertise. This demographic seeks solutions that are easy to deploy, simple to manage, and offer strong protection against evolving threats, often preferring subscription-based models.
Beyond organizational size, the specific needs of various industries drive demand. The Banking, Financial Services, and Insurance (BFSI) sector, with its handling of highly sensitive financial data, demands the highest levels of security and compliance, making NAC a core component of their security architecture. Healthcare organizations, dealing with protected health information (PHI), require NAC for HIPAA compliance and safeguarding patient data across interconnected medical devices and systems. Government and public sector entities rely on NAC to secure critical national infrastructure and classified information. Furthermore, industries like IT & Telecommunications, Manufacturing (especially with the rise of IoT and Industry 4.0), and Retail & E-commerce (for protecting customer data and POS systems) are prime potential customers, all unified by the fundamental need to control and monitor who and what accesses their network resources to prevent data breaches and ensure operational continuity.
| Report Attributes | Report Details |
|---|---|
| Market Size in 2025 | USD 2.9 Billion |
| Market Forecast in 2032 | USD 7.4 Billion |
| Growth Rate | 14.8% CAGR |
| Historical Year | 2019 to 2023 |
| Base Year | 2024 |
| Forecast Year | 2025 - 2032 |
| DRO & Impact Forces |
|
| Segments Covered |
|
| Key Companies Covered | Cisco Systems Inc., Hewlett Packard Enterprise Development LP (Aruba Networks), Forescout Technologies Inc., Pulse Secure LLC (Ivanti), Fortinet Inc., Sophos Group plc, Check Point Software Technologies Ltd., Palo Alto Networks Inc., Extreme Networks Inc., SentinelOne Inc., CommScope Inc. (Ruckus Networks), Genians Inc., InfoBlox Inc., Portnox, Cloudflare Inc., Zscaler Inc., FireEye Inc. (Mandiant), Broadcom Inc. (Symantec), Microsoft Corporation, VMware Inc. |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Enquiry Before Buy | Have specific requirements? Send us your enquiry before purchase to get customized research options. Request For Enquiry Before Buy |
Network Access Control Market Key Technology Landscape
The Network Access Control market is defined by a dynamic and evolving technology landscape, leveraging several core and emerging technologies to deliver robust security. At its foundation, NAC relies heavily on advanced authentication and authorization protocols, including 802.1X, MAC Authentication Bypass (MAB), and Web Authentication (Captive Portal), which ensure only legitimate users and devices gain network access. Endpoint visibility and profiling technologies, often incorporating deep packet inspection and device fingerprinting, are critical for identifying and categorizing every device connected to the network, whether it is a corporate laptop, an IoT sensor, or a personal mobile device. Policy enforcement engines are another key component, translating security policies into actionable network controls, such as VLAN assignment, firewall rule modifications, and access restrictions.
Beyond these foundational elements, the modern NAC technology landscape is increasingly incorporating cutting-edge advancements. Artificial Intelligence (AI) and Machine Learning (ML) are becoming indispensable for enhancing threat detection, identifying anomalous behavior, and automating policy adaptation. These technologies enable NAC systems to learn normal network patterns and user behaviors, allowing for the proactive identification of sophisticated threats and the dynamic adjustment of access policies in real-time. Cloud-native architectures are also gaining prominence, offering NAC solutions as a service (NACaaS) that provide scalability, flexibility, and reduced infrastructure overhead, catering to organizations adopting hybrid and multi-cloud strategies.
Furthermore, integration capabilities with other security solutions are paramount. Modern NAC systems are designed to seamlessly integrate with Security Information and Event Management (SIEM) systems for centralized logging and correlation, firewalls for perimeter defense, Identity and Access Management (IAM) platforms for unified user management, and Endpoint Detection and Response (EDR) solutions for comprehensive endpoint security. Orchestration and automation capabilities are also key, enabling NAC to automate responses to security incidents, such as quarantining non-compliant devices or updating firewall rules, thereby reducing manual intervention and accelerating incident response times. This interconnected technological ecosystem ensures that NAC operates as an integral and intelligent component of an organization's overall cybersecurity posture, providing comprehensive protection across the entire network fabric.
Regional Highlights
- North America: This region is a dominant force in the Network Access Control market, driven by a high concentration of sophisticated IT infrastructure, stringent regulatory compliance mandates (e.g., HIPAA, SOX, NIST), and a pervasive awareness of cybersecurity threats. The presence of numerous key players and early adoption of advanced security technologies contribute significantly to its market share. The United States, in particular, leads in cybersecurity investments and innovation.
- Europe: Europe represents another substantial market for NAC, characterized by strong regulatory frameworks like the General Data Protection Regulation (GDPR), which necessitates robust access control measures. Countries such as the UK, Germany, and France are significant contributors, with a growing focus on data privacy and digital sovereignty. The region is seeing increased adoption due to rising cyberattacks and the need to secure critical infrastructure.
- Asia Pacific (APAC): Expected to be the fastest-growing region, APAC is experiencing rapid digital transformation, increasing internet penetration, and significant investment in IT infrastructure. Emerging economies like China, India, Japan, and Australia are driving demand for NAC solutions as organizations address evolving cyber threats and aim for enhanced data security amidst rapid economic growth and urbanization.
- Latin America: This region is showing promising growth, albeit from a smaller base, primarily driven by increasing digitalization across industries and a growing recognition of cybersecurity risks. Countries like Brazil and Mexico are leading the adoption as businesses invest in modernizing their IT security landscapes to combat rising cybercrime.
- Middle East and Africa (MEA): The MEA market for NAC is expanding steadily, propelled by significant government investments in smart city initiatives, critical infrastructure projects, and diversification of economies away from oil. Cybersecurity initiatives in countries like UAE, Saudi Arabia, and South Africa are fostering a greater demand for advanced NAC solutions to protect burgeoning digital assets.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Network Access Control Market.- Cisco Systems Inc.
- Hewlett Packard Enterprise Development LP (Aruba Networks)
- Forescout Technologies Inc.
- Pulse Secure LLC (Ivanti)
- Fortinet Inc.
- Sophos Group plc
- Check Point Software Technologies Ltd.
- Palo Alto Networks Inc.
- Extreme Networks Inc.
- SentinelOne Inc.
- CommScope Inc. (Ruckus Networks)
- Genians Inc.
- InfoBlox Inc.
- Portnox
- Cloudflare Inc.
- Zscaler Inc.
- FireEye Inc. (Mandiant)
- Broadcom Inc. (Symantec)
- Microsoft Corporation
- VMware Inc.
Frequently Asked Questions
Analyze common user questions about the Network Access Control market and generate a concise list of summarized FAQs reflecting key topics and concerns.What is Network Access Control (NAC) and why is it important?
Network Access Control (NAC) is a security solution that restricts network access to authorized users and devices while ensuring their compliance with security policies. It's crucial for preventing unauthorized access, mitigating insider threats, securing IoT/BYOD devices, and meeting regulatory compliance, thereby enhancing overall network security and reducing the attack surface.
How does NAC contribute to a Zero Trust security model?
NAC is a foundational component of Zero Trust, continuously verifying every user and device attempting to access network resources, regardless of their location. It enforces strict access policies based on identity, device health, and context, effectively embodying the "never trust, always verify" principle central to Zero Trust architectures.
What are the key benefits of implementing a NAC solution?
Implementing NAC offers several key benefits, including enhanced network visibility, automated policy enforcement, improved threat containment through real-time detection and response, streamlined compliance reporting, and robust security for diverse endpoint environments like BYOD and IoT devices. It helps proactively manage security risks and operational efficiency.
What are the main challenges in deploying and managing NAC?
Key challenges include the complexity of integrating NAC with existing IT infrastructure and legacy systems, the potential for network disruption during initial deployment, high upfront costs, and the need for specialized expertise in configuration and ongoing management. Maintaining accurate device profiles and policy updates in dynamic environments can also be complex.
How will AI and Machine Learning impact the future of NAC?
AI and Machine Learning will significantly enhance NAC by enabling predictive threat detection, automating adaptive policy enforcement, reducing false positives, and providing deeper contextual awareness for access decisions. This will lead to more intelligent, proactive, and efficient NAC systems capable of defending against evolving and sophisticated cyber threats.
To check our Table of Contents, please mail us at: sales@marketresearchupdate.com
Research Methodology
The Market Research Update offers technology-driven solutions and its full integration in the research process to be skilled at every step. We use diverse assets to produce the best results for our clients. The success of a research project is completely reliant on the research process adopted by the company. Market Research Update assists its clients to recognize opportunities by examining the global market and offering economic insights. We are proud of our extensive coverage that encompasses the understanding of numerous major industry domains.
Market Research Update provide consistency in our research report, also we provide on the part of the analysis of forecast across a gamut of coverage geographies and coverage. The research teams carry out primary and secondary research to implement and design the data collection procedure. The research team then analyzes data about the latest trends and major issues in reference to each industry and country. This helps to determine the anticipated market-related procedures in the future. The company offers technology-driven solutions and its full incorporation in the research method to be skilled at each step.
The Company's Research Process Has the Following Advantages:
- Information Procurement
The step comprises the procurement of market-related information or data via different methodologies & sources.
- Information Investigation
This step comprises the mapping and investigation of all the information procured from the earlier step. It also includes the analysis of data differences observed across numerous data sources.
- Highly Authentic Source
We offer highly authentic information from numerous sources. To fulfills the client’s requirement.
- Market Formulation
This step entails the placement of data points at suitable market spaces in an effort to assume possible conclusions. Analyst viewpoint and subject matter specialist based examining the form of market sizing also plays an essential role in this step.
- Validation & Publishing of Information
Validation is a significant step in the procedure. Validation via an intricately designed procedure assists us to conclude data-points to be used for final calculations.
×
Request Free Sample:
Related Reports
- Network Access Control Market Size, Share, Trends, & Covid-19 Impact Analysis By Type (Hardware, Software, Services), By Application (Banking, Financial services and Insurance (BFSI), Government, Healthcare, Colleges and universities, Others), By Region - North America, Latin America, Europe, Asia Pacific, Middle East, and Africa | In-depth Analysis of all factors and Forecast 2023-2030
- Airport and Marine Port Security Market Size, Share, Trends, & Covid-19 Impact Analysis By Type (Airport, Marine Port), By Application (TechnologySurveillance Systems, Screening and Scanning Systems, Network Access Control and Security, Physical Access Control Systems, Perimeter Intrusion Detection System, Real-Time Location Systems), By Region - North America, Latin America, Europe, Asia Pacific, Middle East, and Africa | In-depth Analysis of all factors and Forecast 2023-2030
- Network Access Control (NAC) Market Size, Share, Trends, & Covid-19 Impact Analysis By Type (Hardware, Software, Services), By Application (BFSI, Government, Healthcare, Colleges and Universities, Other), By Region - North America, Latin America, Europe, Asia Pacific, Middle East, and Africa | In-depth Analysis of all factors and Forecast 2023-2030
Select License

Why Choose Us

We're cost-effective and Offered Best services:
We are flexible and responsive startup research firm. We adapt as your research requires change, with cost-effectiveness and highly researched report that larger companies can't match.

Information Safety
Market Research Update ensure that we deliver best reports. We care about the confidential and personal information quality, safety, of reports. We use Authorize secure payment process.

We Are Committed to Quality and Deadlines
We offer quality of reports within deadlines. We've worked hard to find the best ways to offer our customers results-oriented and process driven consulting services.

Our Remarkable Track Record
We concentrate on developing lasting and strong client relationship. At present, we hold numerous preferred relationships with industry leading firms that have relied on us constantly for their research requirements.

Best Service Assured
Buy reports from our executives that best suits your need and helps you stay ahead of the competition.

Customized Research Reports
Our research services are custom-made especially to you and your firm in order to discover practical growth recommendations and strategies. We don't stick to a one size fits all strategy. We appreciate that your business has particular research necessities.

Service Assurance
At Market Research Update, we are dedicated to offer the best probable recommendations and service to all our clients. You will be able to speak to experienced analyst who will be aware of your research requirements precisely.
Contact With Our Sales Team
Customer Testimonials
The content of the report is always up to the mark. Good to see speakers from expertise authorities.
Privacy requested , Managing Director
A lot of unique and interesting topics which are described in good manner.
Privacy requested, President
Well researched, expertise analysts, well organized, concrete and current topics delivered in time.
Privacy requested, Development Manager
