Privileged Access Management (PAM) Solution Market Statistics 2025 Analysis By Application (Windows, Unix & Linux, Mac), By Type (Software, Hardware), and By Region (North America, Latin America, Europe, Asia Pacific, Middle East, and Africa) - Size, Share, Outlook, and Forecast 2025 to 2032 (Financial Impact Analysis)
ID : MRU_ 391387 | Date : Apr, 2025 | Pages : 344 | Region : Global | Publisher : MRU
Introduction:
The Privileged Access Management (PAM) Solution market is experiencing significant growth, driven by the increasing need to secure sensitive data and systems from cyber threats. The rise of remote work, the increasing complexity of IT infrastructure, and stringent regulatory compliance mandates are key catalysts for this expansion. Technological advancements, particularly in areas like artificial intelligence (AI) and machine learning (ML), are enhancing PAM solutions effectiveness, enabling more sophisticated threat detection and response capabilities. The market plays a crucial role in addressing global challenges related to data breaches, identity theft, and financial losses associated with compromised privileged accounts. PAM solutions are integral to building robust cybersecurity postures, mitigating risks associated with insider threats, and ensuring compliance with regulations such as GDPR, HIPAA, and PCI DSS. The markets expansion is further fueled by the growing adoption of cloud computing and the increasing reliance on third-party vendors, both of which introduce new security challenges that PAM effectively addresses. Furthermore, the development of more user-friendly and integrated PAM solutions is driving broader adoption across diverse organizations, regardless of size or technical expertise. This increased accessibility is crucial to the widespread adoption needed to truly combat the escalating cybersecurity threats faced globally. The markets future trajectory suggests continued robust growth, driven by heightened cybersecurity awareness, evolving threat landscapes, and the continuous innovation within the PAM sector itself. The seamless integration of PAM with other security solutions, such as SIEM and SOAR, further enhances its value proposition, making it a critical component of a holistic cybersecurity strategy.
The Privileged Access Management (PAM) Solution Market is poised for significant growth from 2025 to 2032, projected at a CAGR of XX%
Market Scope and Overview:
The Privileged Access Management (PAM) Solution market encompasses a range of technologies, applications, and industries. It covers software and hardware solutions designed to control and monitor access to sensitive systems and data by privileged users, including administrators, developers, and third-party vendors. These solutions offer functionalities such as password management, session recording, access control, and vulnerability assessment. Applications span diverse sectors, including finance, healthcare, government, and retail, reflecting the universal need to secure critical systems and data. The markets significance lies in its role in mitigating the risks associated with privileged accounts, which are often targeted by cybercriminals. In the larger context of global trends, the market is responding directly to the growing threat of sophisticated cyberattacks, data breaches, and regulatory scrutiny. The increasing reliance on cloud-based services, the adoption of DevOps practices, and the growing number of interconnected devices further amplify the need for robust PAM solutions. The markets growth trajectory is closely tied to the evolution of cybersecurity threats, emphasizing its importance as a critical component of any comprehensive cybersecurity strategy in our increasingly digital world. This includes the importance of protecting against both internal and external threats, highlighting the sophisticated nature of modern cyberattacks.
Definition of Market:
The Privileged Access Management (PAM) Solution market refers to the industry encompassing the provision of technologies and services designed to manage and control access to privileged accounts and sensitive systems. This includes the management of passwords, session recordings, access control policies, and auditing functionalities. Components of this market include software solutions (e.g., password vaults, session management tools, access governance platforms), hardware components (e.g., secure access devices, network appliances), and professional services (e.g., implementation, integration, and training). Key terms associated with this market include privileged accounts, least privilege access, session monitoring, password management, multi-factor authentication (MFA), access governance, risk and compliance (GRC), and vulnerability management. Understanding these terms is crucial for comprehending the functionality and importance of PAM solutions. The market operates within the broader cybersecurity ecosystem, interacting with other security technologies and processes to achieve a holistic security posture. This includes aspects like identity and access management (IAM), Security Information and Event Management (SIEM), and Security Orchestration, Automation, and Response (SOAR). The markets success relies on effectively addressing the challenges posed by the increasing complexity of IT environments and the evolving nature of cyber threats.
Market Segmentation:
The Privileged Access Management (PAM) Solution market can be segmented by type, application, and end-user. These segments provide a granular understanding of the diverse applications and users contributing to market growth. Each segment exhibits unique characteristics and growth drivers, influencing overall market dynamics. Analyzing these segments allows for targeted marketing strategies, investment decisions, and a better understanding of the markets potential.
By Type:
Software: This segment dominates the market, offering a range of solutions including password vaults, session management tools, and access governance platforms. These software solutions provide centralized control over privileged accounts, facilitating secure access management and auditing capabilities. They are scalable, cost-effective, and adaptable to diverse organizational needs, making them a preferred choice for many businesses.
Hardware: This segment includes physical security devices such as secure access devices (SADs) and network appliances that provide an extra layer of security for privileged access. These solutions typically enhance authentication, encryption, and secure remote access capabilities, providing a strong security foundation in addition to software solutions. They are often used in conjunction with software-based solutions to improve overall security postures.
By Application:
Windows, Unix & Linux, Mac: PAM solutions are designed to support different operating systems, providing comprehensive coverage across diverse IT infrastructures. Each operating system presents unique security challenges, requiring specialized solutions to effectively manage privileged access and mitigate potential vulnerabilities.
By End User:
Governments, Businesses, and Individuals: Governments require robust PAM solutions to secure sensitive national data and infrastructure. Businesses across various sectors leverage PAM to protect their assets and comply with regulations. Individuals, particularly in high-security contexts, can also benefit from PAM solutions for personal data protection. The adoption rate across these end-users varies based on factors such as security awareness, regulatory requirements, and budget constraints.
Market Outlook and Projections:
| Report Attributes | Report Details |
| Base year | 2024 |
| Forecast year | 2025-2032 |
| CAGR % | XX |
| Segments Covered | Key Players, Types, Applications, End-Users, and more |
| Major Players | IBM, Broadcom, Wallix, CyberArk, Centrify, ManageEngine, ARCON, Hitachi ID Systems, Thycotic, Devolutions, One Identity, Ekran System, Jumpcloud |
| Types | Software, Hardware |
| Applications | Windows, Unix & Linux, Mac |
| Industry Coverage | Total Revenue Forecast, Company Ranking and Market Share, Regional Competitive Landscape, Growth Factors, New Trends, Business Strategies, and more |
| Region Analysis | North America, Europe, Asia Pacific, Latin America, Middle East and Africa |
The Top Key Market Players for Privileged Access Management (PAM) Solution Market Listed are:
IBM
Broadcom
Wallix
CyberArk
Centrify
ManageEngine
ARCON
Hitachi ID Systems
Thycotic
Devolutions
One Identity
Ekran System
Jumpcloud
Market Drivers:
Several factors drive growth in the PAM Solution market. Increased regulatory compliance mandates necessitate stronger security protocols, boosting demand. The rise in cloud computing and the adoption of DevOps practices introduce new security challenges, further accelerating PAM adoption. Growing awareness of cybersecurity threats and the increasing sophistication of cyberattacks are compelling organizations to invest in robust PAM solutions. The integration of AI and ML for improved threat detection and response capabilities also drives innovation and adoption within the market. Finally, the increasing volume and sensitivity of data necessitates stringent security measures, making PAM an essential investment.
Market Restraints:
High initial costs associated with implementation and integration can be a barrier for some organizations. Complexity in deployment and management can also pose challenges, especially for smaller organizations with limited IT expertise. Lack of awareness and understanding about PAM solutions among some businesses also hinders wider adoption. Integration difficulties with existing security infrastructures can create complexities in implementation, requiring careful planning and execution. Finally, geographical limitations and lack of skilled personnel in certain regions can slow down market penetration.
Market Opportunities:
Growing adoption of cloud-based PAM solutions presents significant opportunities. The development of AI-powered threat detection and response capabilities offers further innovation potential. Integration with other security technologies such as SIEM and SOAR enhances the overall value proposition of PAM. Expanding into emerging markets and fostering partnerships with system integrators are further avenues for growth. Continuous innovation and improvements in usability and accessibility will also expand the markets reach.
Market Challenges:
The evolving nature of cyber threats constantly presents new challenges. The need to adapt to new attack vectors and vulnerabilities requires ongoing innovation in PAM solutions. The complexity of managing privileged access across diverse IT environments presents operational challenges. Maintaining compliance with evolving regulations across various jurisdictions requires continuous updates and adjustments to PAM strategies. The shortage of skilled cybersecurity professionals capable of implementing and managing PAM solutions creates a significant workforce challenge. Finally, ensuring seamless integration of PAM with existing security solutions and avoiding conflicts requires careful planning and expertise.
Market Key Trends:
Increased adoption of cloud-based PAM solutions is a key trend. The growing use of AI and ML for enhanced threat detection is another significant trend. The integration of PAM with other security solutions like SIEM and SOAR is gaining momentum. Demand for more user-friendly and easily manageable PAM solutions is increasing. The focus on automation and orchestration to streamline PAM processes is also prominent. Finally, a shift towards a more holistic approach to security, incorporating PAM as a core component, is gaining traction.
Market Regional Analysis:
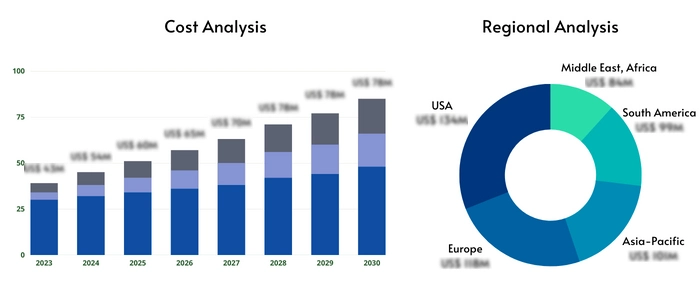
North America currently holds a significant market share due to high cybersecurity awareness and stringent regulatory compliance mandates. Europe is witnessing strong growth driven by the enforcement of GDPR and other data protection regulations. The Asia-Pacific region is expected to experience significant growth due to increasing digitalization and expanding IT infrastructure. Latin America and the Middle East and Africa are showing promising growth potential, although adoption rates may be slower due to factors like lower levels of cybersecurity awareness and economic conditions. Regional variations in cybersecurity regulations, technological infrastructure, and economic conditions influence the market dynamics in each region. The unique security challenges and regulatory landscape of each region require tailored PAM solutions.
Regional Analysis For Privileged Access Management (PAM) Solution Market
- United States, Canada, and Mexico Germany, France, UK, Russia, and Italy China, Japan, Korea, India, and Southeast Asia Brazil, Argentina, Colombia Middle East and Africa
Frequently Asked Questions:
Q: What is the projected CAGR for the Privileged Access Management (PAM) Solution market from 2025 to 2032?
A: The projected CAGR will be inserted here (replace XX with the actual CAGR value).
Q: What are the key trends shaping the PAM market?
A: Key trends include the increasing adoption of cloud-based PAM, the integration with AI and ML for enhanced threat detection, and the convergence with other security tools like SIEM and SOAR. Simplified user interfaces and greater automation are also significant trends.
Q: Which are the most popular PAM solution types?
A: Software-based PAM solutions currently dominate the market due to their flexibility, scalability, and cost-effectiveness. However, hardware-based solutions continue to play a crucial role in enhancing security for high-risk environments.
Q: What are the major challenges faced by the PAM market?
A: The challenges include the ever-evolving threat landscape, the complexity of managing privileged access across heterogeneous IT environments, the skills gap in cybersecurity expertise, and integration complexities with existing security infrastructures.
Q: Which regions offer the greatest growth potential for the PAM market?
A: While North America currently leads in market share, regions like Asia Pacific show significant growth potential driven by increasing digitalization and expanding IT infrastructure. Latin America and the Middle East and Africa also offer emerging market opportunities.
Research Methodology
The Market Research Update offers technology-driven solutions and its full integration in the research process to be skilled at every step. We use diverse assets to produce the best results for our clients. The success of a research project is completely reliant on the research process adopted by the company. Market Research Update assists its clients to recognize opportunities by examining the global market and offering economic insights. We are proud of our extensive coverage that encompasses the understanding of numerous major industry domains.
Market Research Update provide consistency in our research report, also we provide on the part of the analysis of forecast across a gamut of coverage geographies and coverage. The research teams carry out primary and secondary research to implement and design the data collection procedure. The research team then analyzes data about the latest trends and major issues in reference to each industry and country. This helps to determine the anticipated market-related procedures in the future. The company offers technology-driven solutions and its full incorporation in the research method to be skilled at each step.
The Company's Research Process Has the Following Advantages:
- Information Procurement
The step comprises the procurement of market-related information or data via different methodologies & sources.
- Information Investigation
This step comprises the mapping and investigation of all the information procured from the earlier step. It also includes the analysis of data differences observed across numerous data sources.
- Highly Authentic Source
We offer highly authentic information from numerous sources. To fulfills the client’s requirement.
- Market Formulation
This step entails the placement of data points at suitable market spaces in an effort to assume possible conclusions. Analyst viewpoint and subject matter specialist based examining the form of market sizing also plays an essential role in this step.
- Validation & Publishing of Information
Validation is a significant step in the procedure. Validation via an intricately designed procedure assists us to conclude data-points to be used for final calculations.
Request Free Sample:
Related Reports


We're cost-effective and Offered Best services:
We are flexible and responsive startup research firm. We adapt as your research requires change, with cost-effectiveness and highly researched report that larger companies can't match.

Information Safety
Market Research Update ensure that we deliver best reports. We care about the confidential and personal information quality, safety, of reports. We use Authorize secure payment process.

We Are Committed to Quality and Deadlines
We offer quality of reports within deadlines. We've worked hard to find the best ways to offer our customers results-oriented and process driven consulting services.

Our Remarkable Track Record
We concentrate on developing lasting and strong client relationship. At present, we hold numerous preferred relationships with industry leading firms that have relied on us constantly for their research requirements.

Best Service Assured
Buy reports from our executives that best suits your need and helps you stay ahead of the competition.

Customized Research Reports
Our research services are custom-made especially to you and your firm in order to discover practical growth recommendations and strategies. We don't stick to a one size fits all strategy. We appreciate that your business has particular research necessities.

Service Assurance
At Market Research Update, we are dedicated to offer the best probable recommendations and service to all our clients. You will be able to speak to experienced analyst who will be aware of your research requirements precisely.
The content of the report is always up to the mark. Good to see speakers from expertise authorities.
Privacy requested , Managing Director
A lot of unique and interesting topics which are described in good manner.
Privacy requested, President
Well researched, expertise analysts, well organized, concrete and current topics delivered in time.
Privacy requested, Development Manager